The Return of the Yeti
破解WIFI密码
tcpdump -r VanSpy.pcapng -w VanSpy_converted.pcap
╰─ aircrack-ng VanSpy.pcapng -w ~/CTF/tools/rockyou.txt |
先转换成pcap
上面的命令不行,用wireshark
Aircrack-ng 1.7 |
Christmas
名称是SSID,也就是FreeWifiBFC
破解完了密码就解密
airdecap-ng Vanspy.pcap -e FreeWifiBFC -p Christmas
得到Vanspy-dec.pcap

逆天
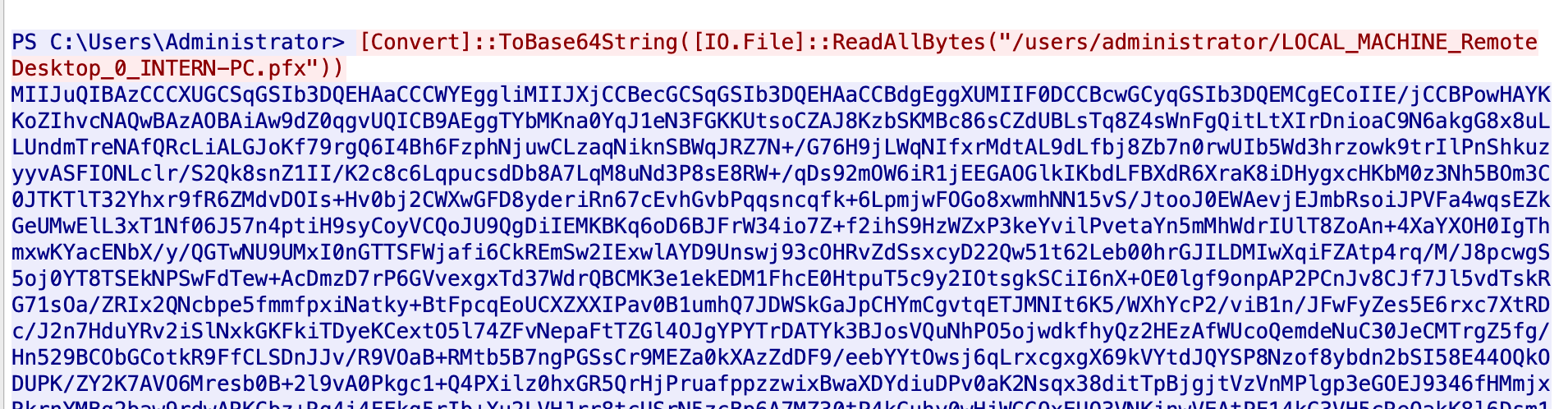
pfx文件

用pfx来解密tls
cat key.pfx | base64 -d > cert.pfx
默认的密码是mimikatz
openssl pkcs12 -in cert.pfx -nocerts -out server_key.pem -nodes
openssl rsa -in server_key.pem -out server.key
导入wireshark

很莫名其妙
拿不到数据,没用windows,败笔了
选这个导出
pyrdp-convert -f replay ext.pcap
np
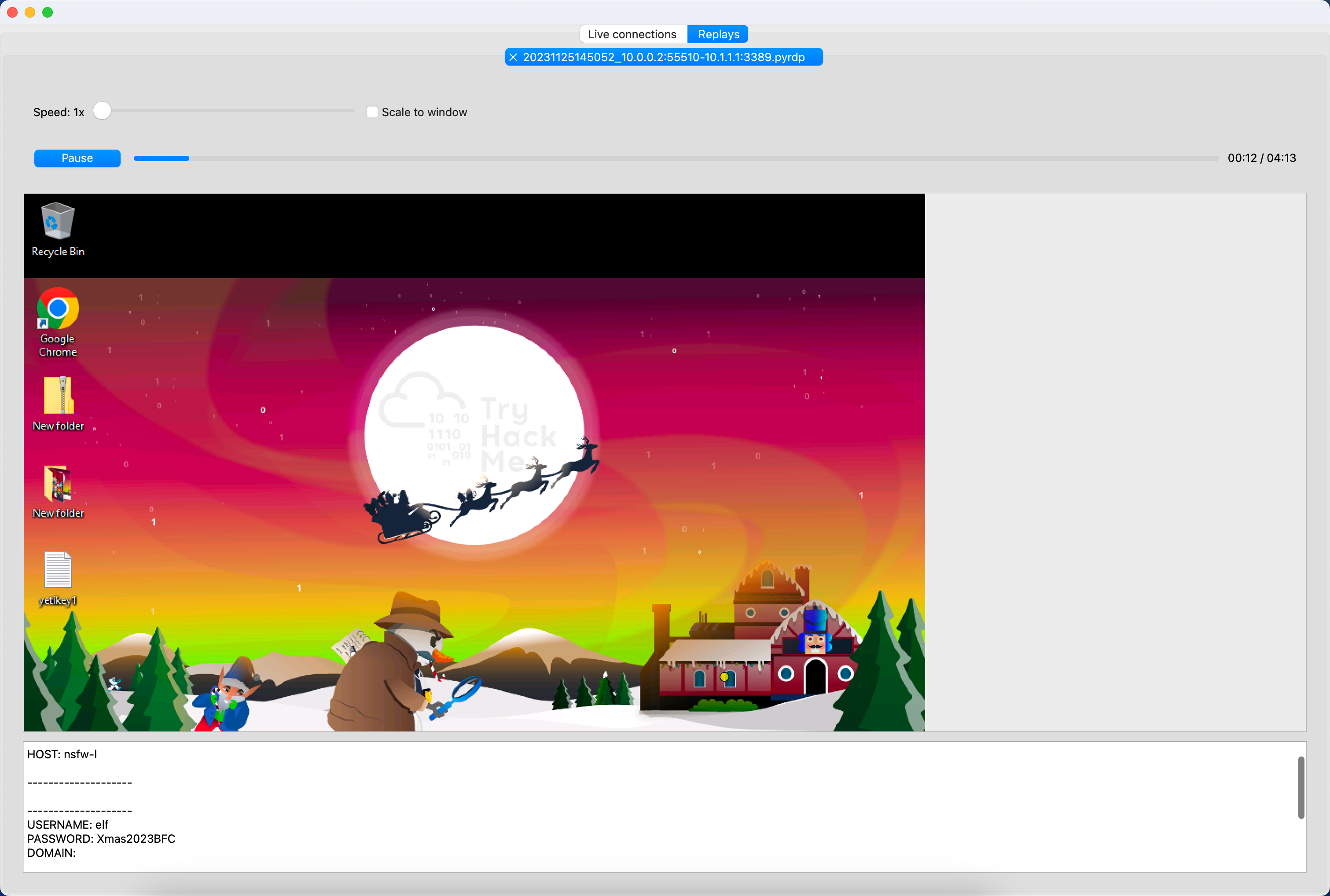
pyrdp-player 20231125145052_10.0.0.2:55510-10.1.1.1:3389.pyrdp
太强了





